| RDB PRIME! Engineering |
|
|
|
|
|
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| It is 08:11 PST on Friday 10/17/2025 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
IA5 (International Alphabet 5) .. to .. Isochronous Ethernet (isoEthernet)
IA5 (International Alphabet 5): IA5 is a seven-bit code that defines the character set used for message transfers, according to the CCITT X.400 Message Handling System (MHS) specifications. In its default coding, IA5 is almost identical to the ASCII system. However, because certain character encodings can be changed, IA5 can take on a non-ASCII form. In particular, the following encodings may be redefined:
One can create and register a particular variant of IA5 encoding, provided that your variant is defined according to these constraints. Various national alphabets have been registered with the ECMA (European Computer Manufacturers Association). A different character set, defined for Teletex (an internatioinal electronic-mail service), uses eight bits, and so provides twice as many possible characters. The Apple Macintosh is another example that uses the encoding of eight bits, that produces an extension to the standard ASCII character set. ICMP:Internet Control Message Protocol -- An integral part of the Internet Protocol (IP) that handles error and control messages. Specifically, gateways and hosts use ICMP to send reports of problems about datagrams back to the original source that sent the datagram. ICMP also includes an echo request/reply (i.e. PING) used to test whether a destination is reachable and responding. IDE (Harddrive):Integrated Device Electronics, the current low-cost storage interface standard for desktop and portable PCs, synonymous with ATA. IDSL:IDSL is a system in which digital data is transmitted at 128 to 144 Kbps on a regular copper telephone line (twisted pair) from a user to a destination using digital (rather than analog or voice) transmission, bypassing the telephone company's central office (CO) equipment that handles analog signals. IDSL uses the Integrated Services Digital Network (ISDN) (Integrated Services Digital Network) Basic Rate Interface in ISDN transmission code. IDSL is a technology developed by Ascend Communications (now part of Lucent Technologies). IDSL is only one possible technology in the Digital Subscriber Line approach (of which Asymmetric Digital Subscriber Line or Asymmetric Digital Subscriber Line is best known) and an expedient approach that allows use of existing ISDN card technology for data-only use. The differences between IDSL and ISDN are:
ISDN Digital Subscriber Line provides DSL technology over existing ISDN lines. Even though the transfer rates for IDSL are about the same as ISDN (144kbps v. 128kbps), and IDSL circuits typically only carry data (not voice), the major benefits of switching to IDSL from ISDN are always-on connections, thus eliminating call setup delays; flat rate billing, instead of per minute fees; and transmission of data over the data network, rather than the PSTN. IEEE:Institute of Electrical and Electronic Engineers (IEEE) An association of engineering societies that develops industry standards. The IEEE 802 committee defined many of the standards for today's local area networks. It is also an international professional society establishing standards in several areas; of particular importance, as stated above, are the IEEE 802 LAN and MAN standards. IEEE 802.6:The IEEE standard for a metropolitan area network, employing the Distributed Queue Dual Bus; 802.6/DQDB was the initial technology platform specified for the Switched Multimegabit Data Service and Connectionless Broadband Data Service. IEEE 802.9:The IEEE standard for an integrated services local area network. IEEE 802.9a:A supplement to the IEEE 802.9 Integrated Services LAN standard specific to IEEE 802.3/Ethernet-style LANs; also referred to as Isochronous Ethernet, isoENET. Impairment:Any of various types of degradation in electrical signals because of interference, loss, or distortion. Signal-to-noise ratio (SNR), echo, and response at different frequencies are examples of impairment measures. Impedance:Impedance is the opposition that alternating electrical current encounters as it moves along a circuit. Impedance is analogous to friction and is one cause of signal attenuation. Impedance represents the ratio of voltage to current along the transmission line, and it is measured in ohms. Factors that determine the impedance of a cable segment include distance between conductors (such as between the signal wire and the conductive shield in coaxial cable), and the type of insulation surrounding the wire. Most network architectures use cable with characteristic impedance. For example, Ethernet cabling is usually 50-ohm, and ARCnet use 93-ohm cable. Implementation Agreements:The specifications created by industry consortia such as the ATM Forum, Frame Relay Forum, and SMDS Interest Group; these groups create specifications outside of the formal standards process, with the original intent that these groups could adopt new protocols faster and more completely than the formal standards groups; these specifications are agreements for protocol and service implementation among the group's members only; the IAs are generally forwarded to formal standards groups for adoption after they are completed. Implicit Congestion Notification:A means of determining that there is congestion on a network. Certain transport protocols, such as TCP from the Internet TCP/IP protocol suite, can infer (derive by reasoning; conclude or accept from evidence or premises) when network congestion is occurring. This notification is in contrast to explicit (plainly expressed; clear) notification methods, such as the ECN (explicit congestion notification) method, used in frame relay networks. In-band Signaling:Signaling and control information that is transmitted at frequencies that lie within the regular, data channel bandwidth, rather than using frequencies that lie outside this bandwidth (as in out-of-band signaling). The term may also be written as in-band signaling. For example, network signaling for in-band signaling that occurs within the user's channel, can be tones within the user's 300- to 3400-Hz voiceband or robbed bits in a T1 carrier. Index of Refraction:A measure of the degree to which light will travel at a different speed in a given medium, such as in water or in a fiber optic core made of a particular type of material (glass or plastic fibers). Information:Data which has been recorded, classified, organized, related, or interpreted within a framework so that meaning emerges. Information Access Attribute (IAA):An attribute of an ISDN bearer service that relates to how the user will access the network across the local user-network interface, such as the channel to use, rate adaption algorithm, and required protocol support; information access attributes do not have to be the same at all user-network interfaces. Information Agent:A program that can search databases for information specified by the users input criteria. The information agent will search a predefined set of databases, or may allow the user to specify the database(s) to use. Information Bit:Bit that is generated by the data source but is not used by the data-transmission system. Information Representation:Networks are typically designed to carry specific types of information representation, for example, analog, analog voice signals, bits, video, or characters. Information System Engineering:The process by which information systems are designed, developed, tested, and maintained. The technical origines of information systems engineering can be traced to conventional informaton systems design and development, and the field of systems engineering. Information systems engineering is by nature structured, iterative, multidisciplinary, and applied. It involves structured requirements analysis and/or engineering, and system testing, documentation, and maintenance. Information systems solve a variety of data, information, and knowledge-based problems. In the past, most information systems were exclusively data-oriented; their primary purpose was to store, retrieve, manipulate, and display data. Application domains included inventory control, banking, personnel record keeping, and the like. The airline reservation system represents the quintessential information system of the 1970s. Since then, expectations as to the capabilities of information systems have risen considerably. Information systems routinely provide analytical support to users. Some of these systems help allocate resources, evaluate personnel, and plan and simulate large events and processes. The users expect information systems to perform all the tasks along the continuum shown in the table below:
Systems engineering extends over the entire life cycle of systems, including:
The systems engineer's perspective is different from that of the product engineer, software engineer/designer, or technology developer. The product engineer deals with detail, whereas the systems engineer takes an overall viewpoint. Systems engineering is based upon the traditional skills of the engineer combined with additional skills derived from applied mathematics, psychology, management, and other disciplines. The systems engineering process is a logical sequence of events/activities and decisions that transform operational needs into a description of system performance and configuration. This process is by its very nature, iterative and multi-disciplinary. Information Theory:Information theory is a branch of the mathematical theory of probability and mathematical statistics, that deals with the concepts of information and information entropy, communication systems, data transmission and rate distortion theory, cryptography, signal-to-noise ratios, data compression, and related topics. It is not to be confused with library and information science or information technology. Claude E. Shannon (1916-2001) has been called "the father of information theory". His theory "considered the transmission of information as a statistical phenomenon" and gave communications engineers a way to determine the capacity of a communication channel in terms of the common currency of bits. The transmission part of the theory is not "concerned with the content of information or the message itself," though the complementary wing of information theory concerns itself with content through lossy compression of messages subject to a fidelity criterion. These two wings of information theory are joined together and mutually justified by the information transmission theorems, or source-channel separation theorems that justify the use of bits as the universal currency for information in many contexts. It is generally accepted that the modern discipline of information theory began with the publication by Claude E. Shannon of his article "The Mathematical Theory of Communication" in the Bell System Technical Journal in July and October of 1948. This work drew on earlier publications by Harry Nyquist and Ralph Hartley. In the process of working out a theory of communications that could be applied by electrical engineers to design better telecommunications systems, Shannon defined a measure of entropy (H):
that, when applied to an information source, could determine the capacity of the channel required to transmit the source as encoded binary digits. Shannon's measure of entropy came to be taken as a measure of the information contained in a message, as opposed to the portion of the message that is strictly determined (hence predictable) by inherent structures, like for instance redundancy in the structure of languages or the statistical properties of a language relating to the frequencies of occurrence of different letter or word pairs, triplets etc. See Markov chains. Entropy as defined by Shannon is closely related to entropy as defined by physicists. Boltzmann and Gibbs did considerable work on statistical thermodynamics. This work was the inspiration for adopting the term entropy in information theory. There are deep relationships between entropy in the thermodynamic and informational senses. For instance, Maxwell's demon needs information to reverse thermodynamic entropy and getting that information exactly balances out the thermodynamic gain that the demon would otherwise achieve. Among other useful measures of information is mutual information, a measure of the correlation between two event sets. Mutual information is defined for two events X and Y as:
where H(X,Y) is the joint entropy or
Mutual information is closely related to the log-likelihood ratio test for multinomials and to Pearson's X2 test. A.N. Kolmogorov introduced an information measure that is based on the shortest algorithm that can recreate it; see Kolmogorov Complexity. Information Transmission Rate:The information transmission rate (in letters per second or words per minute) at which information could be transmitted over a telegraph circuit was initially limited to the rate at which a single human operator would enter a sequence of symbols. An experienced operator could transmit at a speed of 25 to 30 words per minute, which, assuming five characters per word and 8 bits per character, corresponds to 20 bits per second (bps). Interleave (Disk Storage):To arrange data in a noncontiguous way to increase performance. When used to describe disk drives, it refers to the way sectors on a disk are organized. In one-to-one interleaving, the sectors are placed sequentially around each track. In two-to-one interleaving, sectors are staggered so that consecutively numbered sectors are separated by an intervening sector. See diagram below.
The purpose of interleaving is to make the disk drive more efficient. The disk drive can access only one sector at a time, and the disk is constantly spinning beneath the read/write head. This means that by the time the drive is ready to access the next sector, the disk may have already spun beyond it. If a data file spans more than one sector and if the sectors are arranged sequentially, the drive will need to wait a full rotation to access the next chunk of the file. If instead the sectors are staggered, the disk will be perfectly positioned to access sequential sectors. The optimum interleaving factor depends on the speed of the disk drive, the operating system, and the application. The only way to find the best interleaving factor is to experiment with various factors and various applications. RAM Memory can also be interleaved. See interleaved ram storage for more information. Interleave (RAM Storage):Main memory divided into two or more sections. The CPU can access alternate sections immediately, without waiting for memory to catch up (through wait states). Interleaved memory is one technique for compensating for the relatively slow speed of dynamic RAM (DRAM). Other techniques include page-mode memory and memory caches. Intermediate System (IS):In the OSI (Open Systems Interconnection) Reference Model, an Intermediate System is a network entity that serves as a relay element between two or more subnetworks. For example repeaters, bridges, routers, and X.25 circuits are all intermediate systems at the physical, data-link, network, and network layers, respectively. Architecturally, an intermediate system uses at most the bottom three layers of the OSI Reference Model: network, data-link, and physical. These are the so-called subnet layers. This is in contrast to an end system (ES), which uses all seven layers of the model. A node (computer system) is an end system. An intermediate system is also known as a relay open system in the OSI Reference Model. You will also see internetworking unit, or IWU, used to refer to an intermediate system. Also see the OSI Reference Model, and compare to End System (ES). International Alphabet No. 5(IA5):An ISO standard character code, nearly identical to the American Standard Code for Information Interchange (ASCII). International Organization for Standardization (ISO):An international standards organization that comprises national standards bodies; ANSI, for example, is the U.S. representative to ISO. ISO's data communications standards include HDLC, the OSI Reference Model, and various OSI protocol and service definitions. International Telecommunications Union (ITU):The Consultative Committee for Internaltional Telegraph and Telephone (CCITT) is a committee of a United Nations treaty organization called the International Telecommunications Union (ITU). The committee is made up of members from governments and has the task of studying, recommending, and standerdizing technical and operational issues for telecommunications. The United States is involved with the CCITT through the U.S. State Department. The CCITT prepares recommendations that are voted on for approval by the ITU. NOTE: The current trend is to refer to the CCITT standards as ITU standards. Internet:A network made up of two or more interconnected local area or wide area networks. Workstations in each network can share data and devices with other parts of the internet. It is also an international network of networks, all using TCP/IP, and comprises over 80,000 networks and over 10 million hosts. Also called an internetwork. The networks on an internet are connected through routers. A router is a device that physically connects the network cables and maintains network addresses. Data passing from one network to another passes through the router on its way to nodes on another network. Also see router. The Internet -- also known as the Net -- is the world's largest computer network, or net. Actually, the Internet isn't really a network -- it's a network of networks, all freely exchanging information. The networks range from the big and formal, like the corporate networks at AT&T, Digital Equipment, Hewlett-Packard, and Tektronix, to the small and informal, like a couple of computers in a small office, and everything in between. College and university networks have long been part of the Internet, and now high schools and elementary schools are joining up as well. As of August 1993, over 14,000 networks were in the Internet, with 1,000 new networks per month being added. You can think of the Internet as being two things: the people who use it and the information that resides in it. Internet Address (IA):The address of a socket in an Ethernet or AppleTalk internet. This address is made up of the socket number, the node ID of the node in which the socket located, and the network number of the network in which the node is located. The internet address provides a unique identifier for any socket in an Ethernet or AppleTalk internet. See IP address. Internet Assigned Numbers Authority (IANA):The Internet Assigned Numbers Authority (IANA) assigns port numbers, known as well-known port numbers, to specific Application Layer protocols. The table below shows well-known UDP prot numbers used by Windows 2000 components.
http://www.iana.org/assignments/port-numbers for the most current list of IANA-assigned UDP port numbers. Typically, the server side of an Application Layer protocol listens on the well-known port number. The client side of Application Layer protocols uses either the well-known port number or, more commonly, a dynamically allocated port number. These dynamically allocated port numbers are used for the duration of the process and are also known as ephemeral or short-lived ports. The following registry setting determines the range of TCP and UDP prot numbers that TCP/IP uses for Windows 2000. MaxUserPort
Location: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters By default, the maximum port number is 5000. Dynamically allocated port numbers are within the range of 1024 through 5000 (0 through 1023 are reserved for well-known ports controlled by the IANA) Internet Control Message Protocol (ICMP):Even though it is carried inside IP datagrams, the Internet Control Message Protocol is considered to be a parallel protocol running at the network (or internet) layer. It is the method by which routers notify hosts and other routers that a route is unreachable, that there is a problem with a particular path, or that a router is being overloaded. Although it can also be used to provide certain information to hosts (like the current time or the subnet mask for a particular network), these functions are less vital and are often available in other ways. ICMP is another protocol in the TCP/IP suite. As stated above, ICMP is used for error messages such as occur when something is detectably wrong with the packet format, with the selection of a router, or with the condition of some intermediate node in the internet. Such abnormal conditions are reported to the source of the datagram for possible remedial action. For example, if you attempt to connect to a host, the user's system may get back an ICMP message saying "host unreachable" (The table below shows examples of ICMP codes). ICMP can also be used to find out some information about the network. ICMP is similar to UDP (User Datagram Protocol) in that it handles messages that fit in one datagram. However, it is even simpler than UDP. It does not even have port numbers (sockets) in its header (see datagram figure below). Since all ICMP messages are interpreted by the network software itself, no port numbers are needed to say where an ICMP message is supposed to go. ICMP Destination Unreachable Codes:
Even though ICMP is valuable for making routing information available, it is not useful for advertising routes to other networks and other gateways. Most commonly, ICMP is used for these types of functions:
As shown in the figure below, ICMP messages have a simple structure:
A two-byte checksum follows the type and code fields, and the contents of the ICMP message will vary, but will always include the header and the first eight bytes of the datagram that caused the error message to be sent. ICMP provides no error correction, but rather simply reprots routing errors back to their source. By including the header and first eight bytes of the offending datagram, higher level protocols (like TCP) are able to examine their own headers, which are usually included in the first eight bytes, and take corrective action based on the ICMP message. Other contents may include the IP addresses of intervening routers between systems or a list of available routers on a network with corresponding preference levels. Ground Rules for ICMP Mostly to avoid having the cure be worse than the disease, ICMP has certain limitations built into the specification. For one thing, ICMP error messages cannot beget ICMP error messages. For another, broadcast or multicast messages also cannot beget ICMP error messages. Both of these rules help avoid "broadcast storms" that can easily flood a network. Unreachability Messages These generally indicate that there has been a failure somewhere in the process of addressing the datagram that triggers the message. For instance, incorrectly addressed datagrams will cause unreachable messages to be sent. More often, the message indicates that the host or the network is unreachable or unknown. This can happen when a host is simply turned off, when a network link is down, or even when the specified protocol is not available (for instance, attempting to connect to a network application port that is prohibited or restricted). ICMP Routing Messages The most obvious routing messages include requests for a list of available routers and replies that include lists of other available routers along with a priority number for each router. Hosts sometimes make these requests when they boot up to initialize their routing tables; likewise routers advertise gateways when they boot up. Routers also periodically broadcast this information. These routing messages include a field to indicate how long to retain the enclosed information because sometimes routers fail, are taken down, become overloaded, or lose connectivity to remote networks. By periodically broadcasting the current routing preferences, routers ensure that hosts on their networks don't attempt to use a default router that is inappropriate. Another type of routing message is generated when a router becomes overloaded, whether from a high-volume stream of traffic from a single host or from a generally high load generated by many hosts on the network. Routers attempt to process all network traffic as it is received, but when volume is high, this is not always possible. The use of memory buffers to store incoming traffic prior to processing can help, but it no longer takes a Cray or Thinking Machines supercomputer to saturate a typical 10 Mbps Ethernet wire. Routers may send out source quench messages when they are overloaded (though this is not required). Each time the router receives a datagram it can't handle, it discards the datagram and sends back a source quench message, basically asking the fast transmitter to slow down. The originating host then drops its speed until it stops getting the error messages, slowly building up speed again until it starts getting the error messages again. Another instance where an ICMP message may carry routing information occurs when a host sends traffic to one router when a different router advertises a better route (a route with fewer hops). This is called a redirect. This is a common occurrence on networks with more than one router, where the hosts start out with only a single default router in their routing tables. The figure below demonstrates this situation. Host A1 is attempting to send a datagram to Host C and is using Router AB as a default gateway. Since Host A knows that the datagram is destined for a nonlocal network, its sends it to the default gateway. However, Router AB has to route that datagram to Router AC to get it to Host C, taking an extra step (the first step is from Host A to Router AB, then Router AB to Router AC, then Router AC to Host C; the optimal route is from Host A to Router AC to Host C).
Redirects occur when a router forwards a datagram onto the same network on which the datagram was received -- to the router this means that the originating host could have sent the traffic directly to another router on the same network. The router still forwards the datagram, and it also generates a message back to the originating host that there is a better route. The host then incorporates that new route into its routing table. Internet Protocol (IP):This means Internet Protocol. The main tasks of IP are the addressing of the computers and the fragmentation of packets; it contains no functions for end-to-end message reliability or for flow control. IP makes the 'best effort' to forward packets to the next destination, although this forwarding is not guaranteed. Here is a summary of the main attributes of IP:
Basically it is a protocol located in layer 3 of the TCP/IP protocol suite, used to provide connection-less transmissions of data packets over a TCP/IP network. Internet Registry (IR):A central database that contains the network addresses of machines and ID numbers of autonomous systems (domains) on the Internet. The task of maintaining the Internet Registry is delegated by the Internet Assigned Numbers Authority (IANA) and is being carried out by the Defense Data Network Network Information Center (DDN NIC). This process has become considerably more difficult as the corporate world joins the Internet, wanting to use its trademarked names, and willing to put its lawyers to work to get its way. Internet Router (IR):In an AppleTalk internetwork, a device that uses network numbering to filter and route packets. Interoperability:Interoperability in data communications is defined as the communication and intelligent interaction between dissimilar network architectures, protocols, and systems linked by some common medium. This medium can take the form of an operating system, protocol, architecture, logical connection, or physical connection. The medium may even be as simple as network interface cards which support the same protocol. Some difficulties encountered in providing interoperable networks include the large investment, multiple standards and protocols to support and convert, changing business requirements, lack of network management and design tools, and simple network inconsistencies. Open systems become increasingly important as the number of protocols and applications interacting in the wide area network increase. Internetwork Or Internet:A network that consists of two or more smaller networks that can communicate with each other, usually over a bridge, router, or gateway. Internetworking is one of the major buzzwords in the world of networking. Implementing the concepts behind the term is one of the major problems and sources of confusion in the world of networking. Internetworking is the process of establishing and maintaining communications, and of sending data among multiple networks. The goal in an internetworking task is to get data from one user (the source) to another (the destination). This is known as ene-to-end service. Stating the goal is easy; accomplishing it is something alltogether. The details of how to provide the end-to-end service depends to a large extent on the ends, but also on the intermendiaries: the nodes and other devices encountered olong the way. The following types of connections are common:
The details of how to accomplish internetworking connections have filled many thousands of pages, because internetworking can take many forms and may take place at many of several layers. For example, for relay systems such as X.25, the internetworking takes place through the three lowest layers of the OSI (Open Systems Interconnection) Reference Model. In particular, X.25 protocols operate at the network layer. In contrast, for Message Handling Systems such as the CCITT X.400 recommendations, communications between networks may take place at the application layer. In all cases, however, the lower layers eventually need to get involved in order to do the actual relaying of pakets.
Connectionless and Connection-Oriented Services:
Connection-Oriented Services: When the network services are connection-oriented, a temporary (for the duration of the communication) path is established, and data is relayed along this connection. Because the path is preestablished, certain routing information can be assumed, which simplifies the packets that need to be constructed and sent. In all acceptable internetworking implementations, these details should be completely transparent to the users. As far as user are concerned, the connection between the endpoints is direct. Because connection-oriented services are so tidy, it is easier to do error-checking and flow control. Various protocols have been developed to provide connection-oriented services. For example, the CCITT's X.25 is a connection-oriented network layer protocol, as is CONP (Connection-Oriented Network Protocol). The X.25 protocol has been adapted for connection-oriented services by both the OSI and the Internet Communities. COTP (Connection-Oriented Transport Protocol) is a protocol for the transport layer. The NetWare SPX (Sequenced Packet Exchange) protocol is connection-oriented.
Connectionless-Oriented Services: In connectionless service, data trnasmission does not need to wait for a path to be established. Packets are routed independently to their destinations, so that two packets from the same message or transmission might take two different paths. Because packets travel independently, they probably will not arrive in order. Comsequently, the original sequence needs to be reconstructed at the destination end. This is generally done at the transport layer in the OSI (Open Systems Interconnection) Reference Model. CLNP (Connectionless-Mode Network Protocol), CLTP (Connectionless-mode Transport Protocol), and UDP (User Datagram Protocol) are connectionless service protocols. The first two are used in OSI environments; the UDP is usd in TCP/IP (Transmission Control Protocol/Internet Protocol) based environments. The IPX (Internetwork Packet Exchange) and the MHS (Message Handling Service) protocols are two examples of connectionless NetWare protocols.
Internetworking features: Internetworking may involve only local networks, or there may be long-distance connections between networks, so that WAN connections come into play. Paths between endpoints can get quite long, particularly if there are many networks between the two end users. Regardless of the layer under consideration or of the types of networks involved, the internetworking process always has the same type of structure:
The figure below "Layer-Oriented View of an Internetworking Path" shows the elements involved in an internetworking process. Note that the service users need to know nothing about the details of the transmission path.
In addition, several features are desirable in any internetworking service:.
PRIMARY SOURCES
ISO (International Standardization Organization) documents 8208 and 8878 (X.25); SEE ALSO Internetwork Link COMPARE Interoperability Inverse Multiplexer:An inverse multiplexer provides a high-speed data path between computers. It takes a high-speed line and separates it into multiple low-speed lines. The multiple low-speed lines are then recombined by another inverse multiplexer before making connection with the other computer. I/O:I/O is the term input/output (I/O) refers generally to movement into and out of he computer's CPU/memory system. Since this frequently to and from disks, it is often called disk I/O, although I/O can also refer to printer, to network connections, etc. IPFORWARDING:It is part of the options under BSD TCP/IP sofeware variables allowed from within the kernel configuration file. Basically it is an option statement. This parameter determines whether the system forwards IP datagrams destined for another computer. By default, the system forwards datagrams only if it has more than one network interface; i.e., the system is assumed to be a gateway. The default value for the IPFORWARDING variable is 0. The value 1 means always forward datagrams; the value -1 means never forward datagrams. Usually you don't force a system with a single network interface to forward datagrams. Doing this can hide configuration problems on other systems on the network. If the other systems are incorrectly delivering datagrams to your host, forwarding the datagrams will make it appear as if they were correctly addressed and make it difficult to detect the real problem. However, on occasion, you might want to force a system not to forward datagrams by setting this variable to -1. This is useful if you want to prevent a multi-homed host (a host with two network interfaces) from acting as a gateway, but more like a firewall. IP Address:The 32-bit address assigned to hosts that want to participate in a TCP/IP internet. IP addresses are the abstraction of physical hardware addresses just as an internet is an abstraction of physical networks. Actually assigned to the interconnection of a host to a physical network, an IP address consists of a network portion and a host portion. The partition makes routing efficient. The Internet Protocol moves data between hosts in the form of datagrams. Each datagram is delivered to the address contained in the Destination Address (word 5) of the datagram's header. The Destination Address (DA) is a standard 32-bit IP address that contains sufficient information to uniquely identify a network and a specific host on that network. IPX (Internetwork Packet Exchange):A network layer protocol used by Novell NetWare to provide functions for addressing, routing, and switching packets. ISDN (Integrated Services Digital Network):ISDN is a potential telecommmunications standard that is capable of sending digitally econded voice, data, video, and other signals on the same lines. ISDN can also provide access to a variety of communications, information processing, and supplementary services. The table below "Context and Properties of ISDN" summarizes the characteristics of ISDN. Integrated Services Digital Network (ISDN) is a technology that has been devised to allow people access to much higher data speeds using existing telephone lines. CONTEXT AND PROPERTIES OF ISDN:
ISDN is a completely digital service. An ISDN implementation must provide any adapters needed to translate analog or non-ISDN compatible signals. ISDN has the following features:
ISDN Services ISDN provides access to a wide variety of services: Bearer Services Bearer services are concerned with moving information from one location to another. Several bearers are supported:
Teleservices Teleservices are concerned with processing information in various ways. Teleservices include the following:
Supplementary Services The supplementary services are designed to make it easier to use the bearer and teleservices. Supplementary services include telephony's greatest hits, including caller ID, call forwarding and waiting, and conference calling. ISDN Equipment The CCITT (Consultive Committee for International Telegraphy and Telephony) has provided detailed recommendations concerning the types of equipment that can be used with ISDN and also how to accomplish this. Several categories of equipment are distinguished. The categories and their functions are summarized in the table "ISDN Equipment Categories". The figure "ISDN Hardware and Interfaces" shows how these elements fit together. ISDN EQUIPMENT CATEGORIES
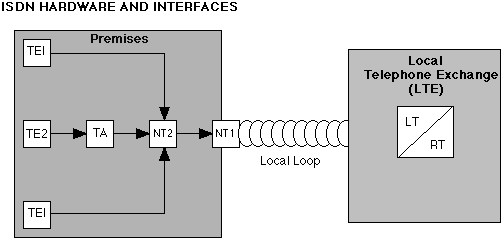 ISDN Transmission Rates ISDN supports either medium- or high- speed transmissions rates. Rates are based on the number of B and D channels allocated. D channels are used for signaling; B (for bearer) channels carry data. D channels may be 16 or 64 kbps; B channels are 64 kbps. The BRI (Basic Rate Interface) rate consists of two B and one 16 kbps D channel (2B+D), which equal a bandwidth of 144 kbps. The configuration of the PRI (Primary Rate Interface) rate depends on where the lines are. In the United States, Canada, and Japan, a PRI line consists of 23B+D. This D channel is 64 kbps, so the PRI rate is 1.536 Mbps. In Europe, the PRI rate is 30B+D, for a bandwidth of 1.920 Mbps. ISDN transmission channels can also be grouped in other ways. The following H channels have been defined:
ISDN has long been popular in Europe, but was always an up-and-coming technology in the United States -- until recently. It has taken several years, but ISDN is finally getting established in North America. This growth is being spurred, in part, by the rapid drop in rates for individual subscribers and also by installation fee waivers being offered as incentives by providers. Its growing popularity is spurring developers and other workers in the field to revise or upgrade existing methods or protocols. For example, in the Internet community, a multilink version of the PPP (Point-to-Point Protocol) has been developed. Despite the healthy growth rate due to its new-found popularity, it's still not clear whether it will be ISDN or its broadband big brother -- broadband ISDN (BISDN) -- that will become the digital technology. Isochronous:Literally meaning same clock, refers to applications where both the source and destination must operate at the same relative rate; voice, for example, is an isochronous service because the source must make samples precisely every 125 µs and the destination must receive those samples so that they may be processed at a relative rate of one every 125 µs; another term for delay-sensitive. isoENET:A variant of Ethernet designed for isochronous (constant rate) transmissions, which are required, for example, when sending video or voice. The isoENET specifications were developed largely by National Semiconductor, and have been submitted as a proposed standard to the IEEE 802.9 committee. These specifications support transmissions using ISDN (Integrated Services Digital Network) signaling methods -- but running over Category 3 UTP (unshielded twisted pair) cable. IsoENET has a 16 Mbps bandwidth, which is broken into two major components. In addition to the 10 Mbps bandwidth for ordinary Ethernet transmissions, isoENET supports up 96 B channels, each with a 64 Kbps capacity -- for a total throughput of about 6 Mbps -- for the isochronous part of the transmission. The Ethernet channel travels just as on an ordinary Ethernet network. The isochronous data is removed at a Hub/Switch, and is sent to a PBX (Private Branch Exchange) or to a TDM (Time Division Multiplexer). The isochronous channel's signaling is compatible with both ISDN and ATM (Asynchronous Transfer Mode) networks. Isochronous Ethernet (isoEthernet):Another name for the IEEE 802.9a standard for an intergrated services LAN operating in conjunction with IEEE 802.3/Ethernet-type devices. See isoENET.
| |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| Back | Home | Top | Feedback | Site Search |
 E-Mail Me |
This site is brought to you by This page was last updated on
09/18/2005 |
This Page has been accessed "7213" times.