| RDB PRIME! Engineering |
|
|
|
|
|
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| It is 14:08 PST on Wednesday 10/15/2025 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Cache .. to .. Cycle, FDDI II
Cache: As a noun, a cache, also known as a disk cache, is an area of RAM (random access memory) set aside for holding data that is likely to be used again and again. By keeping frequently used data in fast RAM, instead of on a hard or floppy disk with much slower access, a system's performace can be improved greatly. As a verb, cache refers to the process of putting information into a cache for faster retrieval. Directory information and hard disk contents are examples of data likely to be cached. The figure below "Disk Cache" shows an example of this process. Cache also refers to a special high-speed storage area. Memory cach is made from SRAM (static random access memory) instead of DRAM (dynamic random access memory). Disk cache refers to the use of memory to hold frequently used information that would take much longer to retrieve if secured directly from the disk. DISK CACHE: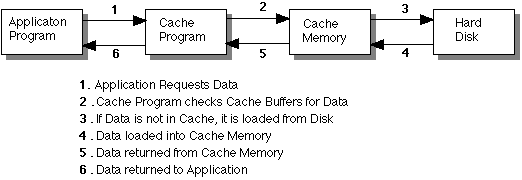 Callback: A security precaution in which a user's pre authorized phone number is verified before allowing the user to connect to a network from a remote location or site. Calendar: (Project Management)A project calendar lists time intervals in which activities in which activities are resources can or cannot be scheduled. A project usually has one default calendar for the normal workweek (Monday through Friday), but may have other calendars as well. Each calendar can be customized with its own holidays and extra workdays. Calendar Unit: (Project Management)The smallest unit of time used in creating the project schedule (typically hours, days, or weeks). Carrier Sense Multiple Access/Collision Detect(CSMA/CD):This is the Ethernet access scheme called Carrier Sense Multiple Access/Collision Detect. It is called this because multiple access points each sense a carrier wave to determine when the network is idle. Each host/device interface that wants to transmit a message listens to the ether to see if a message is being transmitted (i.e., performs carrier sensing). When no transmission is sensed, the host/device interface starts transmitting. Carrier Sensing:A technique that allows multiple devices on a bus type network to gain access to a shared transmission medium. Each device on the network listens until no signals are detected, and then begins transmitting. Transmissions are sent to all connected devices. To receive a transmission, a device must recognize its own address. Carrier Signal:A carrier is a specific frequency in a communication channel that is modulated to carry information. Carrier signals are commonly used in AM, FM, and other radio transmissions to differentiate the signals of each transmitting station. When you turn the dial of a radio, you are selecting a carrier frequency. The radio then amplifies the signal carried on the selected frequency. In amplitude modulation (AM), modulation changes the strength or amplitude of the carrier signal. In frequency modulation (FM), the frequency of the carrier signal is modulated. Cascading Style Sheets (CSS):
The term cascading derives from the fact that multiple style sheets can be applied to the same Web page. CSS was developed by the W3C. A channel is essentially a communication path between two or more devices. In a computer system, a channel provides an input/output interface between the processor and some peripheral device. In telecommunication, a channel may take one of the following forms:
A numbering system used to label or categorized project costs. Typically, the project's chart of accounts is consistent with the overall organization's chart of accounts. Checksum:A small, integer value computed from a sequence of octets by treating them as integers and computing the sum. A checksum is used to detect errors that result when the sequence of octets is transmitted from one machine to another. Typically, protocol software computes a checksum and appends it to a packet when transmitting. Upon reception, the protocol software verifies the contents of the packet by recomputing the checksum and comparing to the value sent. Many TCP/IP protocols use a 16-bit checksum computed with one's complement arithmetic with all integer fields in the packet stored in network byte order. Closing or Closing Out: (Project Management)Obtaining formal approval of the outputs of an activiy, a phase, or the project as a whole, also known as termination. Typically project records are updated and the deliverables are handed off. Circuit: (Fusebox)A grouping of related fuseactions. For example, a ShoppingCart circuit might handle such fuseactions as addItem, removeItem, and display. The fuses that fulfill a circuit's fuseactions are physically located in the same circuit (directory). Each circuit is described by a circuit.xml file, located in the directory specified by the circuit's definition in the fusebox.xml file. Circuit Alias: (Fusebox)The unique name given to each circuit in a Fusebox application. Circuit aliases allow for uniquely identifying ciricuts that have the same directory name such as MyApp/Users and MyApp/Admin/Users. In a compound fuseaction, the first portion of the fuseaction is the circuit alias (e.g. in Cart.addItem, Cart refers to the circuit alias or directory. Circuit Path: (Fusebox)The relative directory path from the root of the Fusebox application to the directory containing a circuit's circuit.xml file (containing its fuseactions) and its fuses (e.g., the circuit path for the circuit, Users, might be specified as MyApp/Admin/Users/). Circuit Media:The primary medium used for communication lines is wire conductors. Wire conductors can be classified into four major groups:
Many factors influence the decision of a medium for a communication network. These factors include cost, speed, expandability, security, distance requirements, environment, maintenance, and leased vs. switched lines. Decisions regarding these factors cannot be made independently. However, for pedagogical reasons, each factor will be considered individually.
Two factors dictate the speed of medium: the response time expected by users and the aggregate data rate. Response time is the time it takes from the moment a terminal sends a request to the time the response from the host gets back to the user. A good response time is two seconds or less. However, longer response times may be tolerated to save on the cost of the medium. Aggregate data rate is the amount of information that can be transmitted per unit of time. A company's users may be satisfied with transmission speeds of 9600 bits per second. But at peak processing times, with large files, the speed requirements may range as high as 19,200 bits per second. The same communication medium may not work for both speeds. Some of the transfer rates for common media are: bps = bits per second Mbps = megabits per second Gbps = Gigabits per second Future expansions must be considered when ever a data communication network is being designed. For example, a company can install twisted pair cable throughout an entire building. Two or three years after installation it finds that it needs coaxial and optical fiber media. In this case the cost of rewiring the building is larger than it would have been to install coaxial and fiber optic initially. When planning communication networks, both short-range and long- range needs must be considered. Providing a completely sealed network where unauthorized persons can never access the network is impossible. However, some media, such as optical fiber, are more difficult to penetrate than other media, such as coaxial cable or satellite. The most vulnerable medium to the average hacker is switched lines. If the line is not leased, then a phone call must be made to the computer that will become the host during the transmission. After the connection is made, digital data is transmitted and routed over any available telephone lines. These types of lines are called switched or dial-up lines because the data transmitted must pass through switching equipment at the phone company so it can be routed to available lines. If a connection between computers needs to kept for very long periods of time such as 12 hours per day or more, and needs to kept during the entire week, then a leased/dedicated line will be more cost effective than a switched line. However, if the connection between computers is performed during short intervals of time or occasionally, the switched line will be a better alternative. A method of network access in which terminals (hosts) are connected by switch together the circuits to which they are attached. In a circuit switched network, the terminals have full "real-time" access to each other up to the bandwidth of the circuit. Circuit Switching is the transfer mode of a network that involves setting up a dedicated end-to-end connection. In a circuit switched network, a central switch is connected to stations in a star configuration. Communication is between the stations and the switch, or the switch establishes circuites between two or mor stations. The stations signal the switch to set up the connection, and when the stations have sent their traffic, they signal the switch to disconnect the circuit. The switch can be a data PBX (Private Branch Exchange), a voice/data PBX, or a telephone central office. In circuit-switched networks, the circuits to the stations (called loops) are not fully utilized. When the circuits are short, the cost of idle time is acceptable, but with long circuits costs may be excessive if usage is light. Utilization can be improved by using a hierarchical network. In a hierarchical network, the switch is placed close to the stations so the circuits can be short and less costly. The more costly long circuits between the switches (called intermachine trunks) are engineered for a higher occupancy rate. Circuit switching connects channels through a centralized switching system. The public switched telephone network is an example of a circuit-switched network. Its primary advantage is worldwide access to any location with telephone service over a well-known addressing scheme. Messages are highly secure, and have exclusive use of the bandwidth. Its disadvantages are cost, limited bandwidth, and inefficient use of the bandwidth. Many observers are predicting the demise of circuit switching, contending that packet switches can do everything circuit switches can, and do it better. It would appear that the major manufacturers agree because all of them are bringing packet switching facilities into their circuit switching systems. CHORUS Nucleus:The CHORUS Nucleus is a microkernel operating system developed by Chorus Systems Inc. of Beaverton, Oregon. The company has developed a microkernel version of UNIX System V, Release 4 called CHORUS/MX V.4 that runs on top of the CHORUS microkernel. The microkernel itself provides fundamental services such as synchronization and preemption management, asynchronous interprocess communication (IPC), remote procedure calls (RPCs), and a low-level hardware supervisor. A virtual memory manager is also available that assists in the movement of objects in distributed environments. The operating system runs as a set of modules on top of the microkernel, and modules communicate through a message-based interface. These modules handle file management, memory management, applications, and networking in distributed environments. Also see Microkernel; UNIX Champion (Project Management):A person with organizational clout who takes on personal responsibility (though not usually data-to-day management) for the successful completion of a project for the organization. Chronon (in temporal databases):A chronon is the shortest duration of time supported by a temporal DBMS -- it is a nondecomposable unit of time. A particular chronon is a subinterval of fixed duration on the time-line. Various models of time have been proposed in the philosophical and logical literature of time. These view time as, among other things, discrete, dnese, or continuous. Intuitively, discrete models of time are isomorphic [a one-to-one correspondence between the elements of two sets such that the result of an operation on elements of one set corresponds to the result of the analogous operation on their images in the other set.] to the natural numbers, that is, there is the notion that every moment of time has a unique successor. Dense models of time are isomorpic to (either) the real or rational numbers: between any two moments of time there is always another. Continuous models of time are isomorphic to the real numbers, that is, they are both dense and also, unlike the rational numbers bave no "gaps". Alternative names are instance, moment, time quantum, time unit. "Instance" and "moment" invite confusion between a point in the continuous model and a nondecomposable unit in the discrete model (-E8 -- names should be intuitive). Clocking instruments invariably report the occurrence of events in terms of time intervals, not time "points". Hence, events, even so-called "instantaneous" events, can best be measured as having occurred during an interval (-E9 -- names should be precise). "Time quantum" is precise but is longer and more technical than "chronon" (-E2 -- names should be easy to write, that is, they should be short or possess a short acronym, should be easily pronounced (the name or its acronym), and should be appropriate for use in subscripts and superscripts). "Time unit" is perhaps less precise (-E9 -- names should be precise). Class: (class:UML, class:Java)An implementation that can be instantiated to create multiple objects with the same behavior. An object is an instance of a class. Types classify objects according to a common interface; classes classify objects according to a common implementation [OMG 1992]. Contains a definition that all objects belonging to the class can follow [Jacobson et al. 1995]. A description of a set of objects that share the same attributes (properties), operations, methods, relationships, constraints, and semantics. A class may use a set of interfaces to specify collections of operations it provides to its environment. UML 2.0 defines a class a s type of classifier that describes a set of objects that share the same features. A class definition defines the instance and class variables and methods available for use in the class, as well as other information such as the immediate superclass. You can use the Java API to view the hierarchy of individual classes and to look up specific methods used by each class. All data and methods (functions) in Java are defined within classes, and a class describes something you want to write programs about. real objects or entities, and business processes or concepts. The attributes and methods of a class should model the real-world objects to the extent necessary for use in applications. Class: (class:OO)A software package that encapsulates methods and variables into a single construct; a blueprint for producing Objects. Mouse is a class; Mickey is an object. In ColdFusion MX, instead of classes, we have components. Client/Server:The model of interaction in a distributed system in which a program at one site sends a request to a program at another site and awaits a response. The requesting program is called the client; the program satisfying the request is called the server. It is usually easier to build client software than server software. Client/Server Computing:Client/Server computing is a networking arrangement with the following characteristics:
Applications capable of running in a client/server environment can be split into a front end that runs on the client and a back end that runs on the server. The front end provides the user with an interface for giving commands and making requestrs. The application's real work is done by the back end, which processes and carries out the user's commands. Client/Server computing allows for several types of relationships between the server and client, including the following:
SEE ALSO Back End; Front End Cluster (Disk Storage):A group of disk sectors. The operating system assigns a unique number to each cluster and then keeps track of files according to which clusters they use. Occasionally, the operating system marks a cluster as being used even though it is not assigned to any file. This is called a lost cluster. You can free up disk space by reassigning lost clusters, but you should first make sure that the clusters do not, in fact, contain valuable data. In DOS and Windows, you can find lost clusters with the ScanDisk utility. DOS and Windows keep track of clusters with the File Allocation Table (FAT). The size of each cluster depends on the disk's partition size. Cluster (Network):In a network, particularly in a mainframe based network, a group of I/O (input/output) devices, such as terminals, computers, or printers, that share a common communication path to a host machine. Communications between the devices in a cluster and the host are generally managed by a cluster controller, such as IBM's 3274 controller. Coaxial Cable:An electrical cable consisting of a central wire surrounded by a second tubular wire made of braided mesh, both of which have the same center point, or axis, hence the name coaxial. Separated from the central wire by insulation, the tubular wire shields electronic impulses traveling along the central wire. In turn, the tubular wire is surrounded by insulation. Put another way, a coaxial cable consists of two conductors. The inner conductor, normally copper or aluminum, is shielded by placing it inside a plastic case or shield. The second conductor is wrapped around the plastic shield of the first conductor. This further shields the inner conductor. Finally, the outer conductor (shield) is covered with plastic or some other protective and insulating cover. Coaxial cables are normally grouped into bundles. Each bundle can carry several thousand voice and/or data transmissions simultaneously. This type of cable has little signal loss, signal distortion, or crosstalk. Therefore, it is a better transmission medium than open wire or twisted pair cables. Coaxial cable comes in different sizes. It is classified by size (RG) and by the cable's resistance to direct or alternating electric currents (measured in ohms, also called impedance). The following are some coaxial cables commonly used in networking:
Coaxial cable has the following characteristics:
As indicated above coax comes in many styles. However, the most commonly used types in computer networking are thicknet and thinnet. WARNING: Do not try to use 75 ohm video cabling in a computer networks. It is more common, but it will not work for computer network devices. COST PER LOCATION: Thinnet coaxial cable has the lowest cost per station of any type of cable, at around $25 dollars. These cables can be purchased with connectors already attached and can be installed by just about anyone; they are simply daisy chained from one computer to another. Installing thicknet coaxial cable typically costs about $50 per station, land transceivers must be included for each station, at a cost of about $100. DISTANCE LIMITATIONS: Thinnet is limited to a total bus distance of 185 meters, while thicknet is limited to 500 meters total. OTHER LIMITATIONS: Because they are bus networks, the path of the installed cable must match the locations of existing computers. For this reason, adding computers that are not near the bus cabling is difficult and expensive. BANDWIDTH: The useful bandwidth of coaxial cabling is 10 Mbps, the speed of Ethernet. No other popular network standard allows the use of coaxial cabling. The theoretical limit, however, may be as high as 550 MHz in point-to-point wiring. ColdFusion:In 1995, J.J. and Jeremy Allaire introduced a product they believed would revolutionize application development for the Web. They too called their creation ColdFusion. The two brothers formed the Allaire Corporation and began selling ColdFusion. Unlike it s infamous namesake, ColdFusion has delivered on the promises put forth by it s creators. In 2001, Macromedia acquired Allaire, and along with it, ColdFusion. ColdFusion MX represents the second ColdFusion product release under the Macromedia banner. According to Macromedia's marketing materials, ColdFusion is "the rapid server scripting environment for creating rich internet applications." Internet applications exist as a collection of pages, also known as templates, which work together to allow users to perform such tasks as reading email, buying books, or tracking packages. Internet applications often act as the front-end to back-end servers, such as legacy applications and databases, and can be accessed through various means such as web browsers, cell phones, and other Internet-enabled devices. Some examples of web sites and applications built using ColdFusion include Autobytel.com's application for researching and purchasing a car (http://www.autobytel.com/). ColdFusion is a web-to-database production tool. ColdFusion is a web application server. A web application server is a middleware application that expands the functionality of web servers by linking them to a wide range of services such as databases, directory systems, search engines, email programs, etc. The web application server also provides a consistent runtime environment for web applications. ColdFusion application middleware can be used to:
ColdFusion is also designed for rapid application development (RAD). ColdFusion abstracts complex, low-level programming tasks, such as establishing connectivity with a mail server or querying a database, with simple HTML-like tags. The result is an application development cycle that is short and to the point. Command Optimization (Harddrive):Commands to a device are queued for immediate execution, without having to wait for responses, increasing performance and making RAID more practical. COmmon Business Oriented Language (COBOL):A business data processing language. It is a high-level programming language, which greatly simplifies computer programming since it allows program instructions to be expressed in a form that resembles human language or the standard notation of mathematics. Designed by a committee of computer manufacturers and users (CODASYL) as an English-like language specifically for business data processing. It is the most widely used programming language for business applications. It is an English-like language that was specifically designed to handle the input, processing, and output of large volumes of alphanumeric data from many data files that is characteristic of business data processing. COBOL was developed and is maintained by the Conference on Data Systems Languages (CODASYL), which is composed of representatives of large computer users, government agencies, and computer manufacturers. The specifications of the COBOL language are, therefore, subject to periodic revision and updating. The American National Standards Institute (ANSI) has developed standards for COBOL that recognize different "levels" and "modules" of COBOL. Standards for a "Minimum Standard" COBOL and "Full Standard" COBOL have also been developed. The COBOL Divisions Every program written in the COBOL language must contain four major parts called "divisions", which are summarized below.
COBOL Procedure Division Statements The procedure Division is the section of a COBOL program that is most like programs written in languages like FORTRAN or BASIC. The major statements in this division of COBOL can be grouped into the following four categories:
The Common Gateway Interface (CGI) is an interface to a Web server that enables a programmer to extend that server's functionality. Using CGI, a designer can interact with users who access a web site. On a theoretical level, CGI enables an designer to extend the capability of a server to parse (interpret) input from the browser and return information based on the users input from said server. On a practical level, CGI is an interface that enables the programmer to write programs that can easily communicate with the Web server. CGI provides a portable and simple solution to interacting with a Web server. The CGI protocol defines a standard way for programs and/or scripts to communicate with the Web server. Without much special knowledge, a programmer can write a program in any computer language that interfaces and communicates with the Web server. This program will work with all Web servers that understand the CGI protocol. CGI communication is handled over the standard input and output, which means that if you know how to print and read data using your programming language, you can write a Web server application. Other than parsing the input and output, programming CGI applications is almost equivalent to programming any other application. For example, if you want to program a "Hello, World" program, you use your language's print functions and the format defined for CGI programs to print the proper message. Because CGI is a "common interface", you are not restricted to any specific computer language. An important question many people ask is what programming languages can you use to program CGI? You can use any language that can do the following:
Almost all programming languages and many scripting languages perform these three activities, and you can use any one of them. Common Object Request Broker Architecture (CORBA):CORBA provides the mechanisms by which objects transparently make requests and receive responses, as defined by OMG's Object Request Broker (ORB). The CORBA ORB is an application framework that provides interoperability between objects, built in (possibly) different languages, running on (possibly) different machines in heterogeneous distributed environments. It is the cornerstone of OMG's Object Management Architecture. The Common Object Request Broker Architecture (CORBA), is the Object Management Group's (OMG) answer to the need for interoperability among the rapidly proliferating number of hardware and software products available today. Simply stated, CORBA allows applications to communicate with one another no matter where they are located or who has designed them. CORBA 1.1 was introduced in 1991 by the Object Management Group (OMG) and defined the Interface Definition Language (IDL) and the Application Programming Interfaces (API's) that enable client/server object interaction within a specific implementation of an Object Request Broker (ORB). CORBA 2.0, adopted in December of 1994, defines true interoperability by specifying how ORBs from different vendors can interoperate. The (ORB) is the middleware that establishes the client-server relationships between objects. Using an ORB, a client can transparently invoke a method on a server object, which can be on the same machine or across a network. The ORB intercepts the call and is responsible for finding an object that can implement the request, pass it the parameters, invoke its method, and return the results. The client does not have to be aware of where the object is located, its programming language, its operating system, or any other system aspects that are not part of an object's interface. In so doing, the ORB provides interoperability between applications on different machines in heterogeneous distributed environments and seamlessly interconnects multiple object systems. In fielding typical client/server applications, developers use their own design or a recognized standard to define the protocol to be used between the devices. Protocol definition depends on the implementation language, network transport and a dozen other factors. ORBs simplify this process. With an ORB, the protocol is defined through the application interfaces via a single implementation language-independent specification, the IDL. And ORBs provide flexibility. They let programmers choose the most appropriate operating system, execution environment and even programming language to use for each component of a system under construction. More importantly, they allow the integration of existing components. In an ORB-based solution, developers simply model the legacy component using the same IDL they use for creating new objects, then write "wrapper" code that translates between the standardized bus and the legacy interfaces. CORBA is a signal step on the road to object-oriented standardization and interoperability. With CORBA, users gain access to information transparently, without them having to know what software or hardware platform it resides on or where it is located on an enterprises' network. The communications heart of object-oriented systems, CORBA brings true interoperability to today's computing environment. Common Management Information Protocol (CMIP):A network management protocol for the OSI Reference Model. CMIP, pronounced "see-mip", defines how management information can be communicated between stations. CMIP is functionally comparable to the older, and arguably more widely used, SNMP (Simple Network Management Protocol). Communication Buffer:RAM (Ramdom Access Memory) set aside on a file server for temporarily holding packets until they can be processed by the server or sent onto the network. The RAM will be allocated as a number of buffers, each with a predetermined size. A communication buffer is also known as a routing buffer or packet receive buffer. Communication Medium:The physical medium over which a communications signal travels. Currently, the most popular medium is cable. Wireless media, such as infrared wave, microwave, or radio wave, are also becoming more widely used. Communication Network:In its simplest form, is a set of equipment and facilities that provides a service: the transfer of information between users located at various geographical points. In data communications the primary networks used are electronic or optical technologies. Examples of such networks include telephone networks, computer networks, television broadcast networks, cellular telephone networks, and the Internet. Communication Time:The time taken to send a message depends upon the length of the message and the type of network being used. It can be calculated using the formula: where Co is a fixed cost of initiating a message, know as the access delay. For example, using an access delay of 1 second and a transmission rate of 10,000 bits per second, we can calculate the time to send 100,000 records, each consisting of 100 bits as: If we wish to transfer 100,000 records one at a time, we get: Clearly, the communication time is significantly longer transferring 100,000 records individually because of the access delay. Consequently, an objective of any database system is to minimize both the volume of data transmitted over the network and the number of network transmissions. Composition: (class:OO)Architecture in which one object is referenced as a property of another object; key difference between aggregation (OO) and composition (OO) is that the included object in a compositon relationship has no independent existence from the referring object. Compound Fuseaction: (Fusebox)A distinction made between earlier versions of Fusebox fuseactions (e.g., addItemToCart) and the new fuseaction nomenclature introduced in Fusebox 3 2001, made up (compunded) of a circuit alias and a fuseaction request, separated by dot notation (e.g., Cart.addItem). In some literature this is referred to as a fully-qualified fuseaction or a circuit-qualified fuseaction. Computer:A computer or computers could be consider a integral part of any data communications network. But in general, a computer has a CPU, Central Processing Unit, MM, main memory, or working memory known as RAM, an ALU, arithmetic logic unit, that can store and process information under program control. Basically, a device that receives, processes, and presents data. The above primarally discribs a digital computer. Most digital computers are occupied with a performing applications related to bookkeeping, accounting, engineering design, or test data reduction, word processing, including the entire concept of office automation. Conductor:Any material (for example, copper wire) that can carry electical current. Compare conductor with semiconductor or insulator. CONFIG.SYS (DOS):In DOS (Disk Operating System) and OS/2 environments, CONFIG.SYS is a file that contains information about various types of configuration and driver settings. For example, CONFIG.SYS may include information about drivers and memory managers that are loaded into memory. The OS/2 configuration file can be quite long and complex. Under Windows NT the use of the CONFIG.SYS is for providing backward-compatible source for locating and setting DOS environment variables. Apart from inherting environment variables and path information, Windows NT otherwise ignores the CONFIG.SYS file. Congestion:In data communications, a state in which the data traffic approaches or exceeds the channel's capacity, resulting in a sever performance degradation and, possibly, loss of packets. Congestion Control:When congestion occurs inside the network as a result of a surge in traffic or a fault in equipment, the network should react by applying congestion or overload control mechanisms to ensure a degree of continued operation in the network. In the case of roads, drivers are insturcted to take a different route or even to stay home! Similarly, during congestion, information traffic may be rerouted or prevented from entering the network. Connection:The path between two protocol modules that provides reliable stream delivery service. In a TCP/IP internet, a connection extends from a TCP module on one machine to TCP module on the other. It could also be thought of as an association between two sockets that facilitates the establishment and maintenance of an exclusive dialog between twoentities. See session. Connection End:In a connection, the communicating socket and the connection information associated with it. Connection Identifier (ConnID):An identification number associated with each connection; a connection provides a unique identifier by using the socket address and ConnID of the two connection ends. Connection-Oriented:Telephone networks are considered connection-oriented because they require the setting up of a connection before the actual transfer of information can take place. Basically in network operations, a connection-oriented service is one in which a connection (a path) must be established between the source and destination before any data transmission takes place. With this service, packets will reach their destination in the order sent, because all packets travel along the same, "no-passing" path. With this type of connection, the OSI (Open Systems Interconnection) data-link layer, for example, checks for errors, does flow control, and requires acknoledgment of packet delivery. X.25 and TCP (Transmission Control Protocol) are two protocols that support connection-oriented services. Connection-oriented services are defined at the network connection-oriented network service (CONS) and transport connection-oriented transport service (COTS) layers. Compare with Connectionless Service, Constructors: (JAVA, UML)When you create an object, a special method called a constructor automatically initializes the object's data members. A constructor, which is identified by the = (equal) new notation, declares the type of data or object to be stored and assignes it a variable name in the computer's memory. A contructor is simply a method with the same as the class of which it is a member. A constructor can take parmeters and be overloaded, but cannot have a return type. A constructor with no parameters defined is sometimes called a no-org constructor for the class. The new operator, followed by a constructor of the class, is what instantiates an object of that class. Examples, follow:
Car red = new Car(); // Use the default constructor A constructor can call another constructor by using the keyword this as a method. If you use it, this() must be the first statment in the constructor. You use this() to reduce code duplication. If you do not write any constructors for your class, the compiler will provide a default constructore with no parameters. However, as soon as you provide any constructor, the compiler will no longer provide the defualt one for you. A message that creates an object, often called a constructor, is represented by a dashed line with an open arrowhead, ss shown below.
an object constructor In network operations, a connectionless service is one in which transmissions take place without a preestablished path between the source and destination. This means that packets may take different routes between the source and destination. Connectionless services are defined at the network and transport layers, with the specifications in Connectionless Mode Network Service (CLNS) and Connectionless Transport Service (CLTS), respectively. Because packets may arrive by different paths and in random sequences, there is no way to guarantee delivery in connectionless service. Instead, the higher layers, particularly the transport layer, are left with the job of making sure packets reach their destination without error. Connectionless Network Protocol (CLNP), Connectionless Transport Protocol (CLTP), Internet Protocol (IP), and User Datagram Protocol (UDP) are all examples, of protocols that support connectionless service. Connectionless Protocols:Is the transport of self-contained messages, i.e. stateless or individual messages are sent. See Connectionless Network Protocol (CLNP), Connectionless Transport Protocol (CLTP), Internet Protocol (IP), and User Datagram Protocol (UDP) are all examples, of protocols that support connectionless service. Consultative Committee on International Telephone & Telegraph (CCITT):A committee formed in 1938 that sets the international standards for the hardware and communications protocols for data and voice transmissions. Content Network:The content network is considered the "pot of gold" by many ISPs/Companies because it is where all ISP/Companes content resides. This network must be highly secure. Design an architecture so that no servers or services from the Internet directly communicate with services or servers on the content network. Centralize content and data on this network to increase manageability and security. The figure below shows a sample content network.
The following paragraphs describe services that typically run on a content network. MailStore The MailStore is the back-end server for email. It contains email messages for all ISP subscribers. For medium-sized and large ISPs, we recommend that some form of high availability (HA) or clustering be implemented with MailStore to enhance reliability and availability. The MailStore interfaces with front-end mail proxies (POP3 and/or IMAP4 servers) for subscriber access to email. Unlike web servers and news servers, large-scale mail servers do not use NFS servers for storage. Large-scale mail servers have their own methods of indexing and storing email messages. File systems configured for MailStore are usually configured with very large numbers of inodes in the inode table. This configuration is due to the inherent characteristic of email, that is, a large number of small files. NFS The NFS allows file access across a network. NFS servers are commonly used for web content and news storage. For ISP environments with static web content, storing content locally on every web server may not be economical or manageable. In these cases, we recommend centralized storage on an NFS server. For large ISPs, NFS servers are often configured with high availability (HA) or in clusters for reliability and availability. This design principle holds true for most, if not all, servers residing in a content network. Relational Database A database is a collection of related information, and databases come in many varieties. Inverted list, hierarchic, and network database models are older types of database systems. These are typically inflexible and difficult to work with. In today's world of information technology, relational databases dominate information management. Relational databases store and present information in tables and hide the complexity of data access from the user, making application development relatively simple. For an ISP infrastructure, the relational database usually resides on the content network. This placement provides fast access to information by users and applications within the infrastructure, while maintaining a secure and centralized environment for data storage. A relational database is usually implemented in a large-scale environment where performance, availability, and manageability are critical to the business and dynamic content generation is required. For static content in a small-scale environment, an NFS server is sufficient. Billing System The billing system is one of the most critical infrastructure services. It facilitates new subscriber registration, customer care, user provisioning, and bill presentment. To achieve a seamless integration, tightly integrate the billing system with the directory server. Also, relational databases are commonly needed for billing platforms and must be integrated with billing software. For small environments, the cost of the billing system can be too steep and not cost-effective to maintain in-house. Many small ISPs outsource this function to application service providers (ASPs). Internal/External DNS The primary DNS is required for zone transfers and zone updates. Place primary DNS servers for both internal and external domains on the content network. While having a primary external DNS server reside at the DMZ is common, we strongly recommend that you place it on the content network. Place only secondary external DNS servers on the DMZ network. (For the benefits of splitting the DNS in this manner, see "DMZ Network".) All zone transfers are one-way from a primary server to one or more secondary servers. A list of secondary servers can be specified to ensure that only authorized secondary servers receive zone data and dynamic updates. When configuring DNS servers, use the following guidelines:
For availability, use front-end load balancers for load distribution. LDAP Master The LDAP master directory is the core of authentication, authorization, and accounting for an ISP. Directory service is considered critical for an ISP. If not designed properly, it can be the single point-of-failure. Design the directory so that it is secure and highly available. The master directory server is usually configured with high availablity (HA) or clusters to ensure availability and reliability. Replicate part or all of the directory information tree (DIT) to authorized replica servers. For optimal performance, point systems to the nearest replicas for LDAP searches and reads. They should not point to the master directory server directly for LDAP queries. Control Packets:Messages that do not contain data, but are used for administrative purposes, such as enquiry, acknowledgment, and notification; control packets are also used to open and close connections. Cookie:This is a mechanism in Netscape Navigator that lets users store small pieces of information on the client computer in a reasonably secure manner. In other words, when you have a need for some tidbit of information to persist at the client level while either loading deverse HTML documents or moving from one session to another, the cookie mechanism saves the day. Netscape's technical documentation (much of which is written from the perspective of a server writing to a cookie) can be found on the Web at http://www.netscape.com/newsref/std/cookie_spec.html. The cookie is commonly used as means to store the username and password you enter into a password-protected World Wide Web site. the first time you enter this information into a CGI-governed form, the CGI program has Navigator write the information back to a cookie on your hard disk (usually after encrypting the password). Rather than bothering you to enter the username and password the next time you access the site, the server searches the cookie data stored for that particular server and extracts the username and password for automatic validation processing behind the scenes. The Cookie File Allowing some foreign CGI program to read from and write to your hard disk may give you pause. But Navigator doesn't just open up your drive's directory for the world to see (or currupt). Instead, the cookie mechanism provides access to just one special text file located in a platform-specific spot on your drive. In Windows versions of Navigator, the cookie file is named cookies.txt and is located in the Navigator directory; Mac users will find the MagicCookie file inside the Netscape folder, which is located within the System Folder:Preferences folder. The cookie file is a text file (but because the MagicCookie file's type is not TEXT, Mac users can open it only via applications capable of opening any kind of file). If curiosity drives you to open the cookie file, it is recommended that you do so only with a copy saved in another directory or folder. Any alteration to the existing file can mess up whatever valuable cookies are stored there for sites you regularly visit. Inside the file (after a few comment lines warning you not manually alter the file) are lines of tab-delimited text. Each return-delimited line contains one cookie's information. The cookie file is just like a text listing of a database. The Cookie Record Among the "fields" of each cookie record are the following:
Notice that cookies are domain-specific. In other words, if one domain creates a cookie, another domain cannot access it through Navigator's cookie mechanism behind your back. This is the reason why it's generally safe to store what is called throwaway passwords (the username/password pairs required to access some free registration-required sites) in cookies. Moreover, sites that store passwords in a cookie usually do so as encrypted strings, making it more difficult for someone to hijack the cookie file from your unattended PC/Mac and figure out what your personal password scheme might be. Cookies also have expiration dates. Because the cookie file can hold no more than 300 cookies (as dictated by Navigator), the cookie file can get pretty full over the years. Therefore, if a cookie needs to persist past the current Navigator session, it also has an expiration date established by the cookie-writer. Navigator cleans out any expired cookies to keep the file from exploding some years hence. Not all cookies have to last beyond the current session, however. In fact, a scenario in which you use cookies temporarily while working your way through a Web site is quite typical. Many shopping sites employ one or more temporary cookie records to behave as the shopping cart for recording items you intend to purchase. These items are copied to the order form at check-out time. But once you submit the order form to the server, that client-side data has no particular value. As it turns out, by not specifying an expiration date, Navigator keeps the cookie fresh in memory without writing it to the cookie file. When you quit Navigator, that cookie data disappears as expected. Cookie Poisoning:When a hacker is using "cookie poisoning", they are usually someone who has authorized access to the Web application in the first place. The hacker is usually a registered customer and is familiar with the application in question. The hacker may alter a cookie stored on their computer and send it back to the Web server. Because the application does not expect changes to the cookie, it may process the poisoned cookie. The effects are usually the changing of fixed data fields, such as changing prices on an e-commerce site or changing the identity of the user logged into the site -- or anyone else the hacker chooses. The hacker is then able to perform transactions using someone else's account information. The ability to actually perform this hack is actually as a result of poor encryption techniques on the Web developer's part. The ease with which these types of hacking are carried out is frightening. These examples should be enough to illustrate why developers need to take application security into consideration in developing their applications. Building checks into systems that verify parameters and check for "illegal" code should complement other security measures that identify and authenticate users to render their information more secure. Taking care to make sure that users cannot purposely or inadvertently "trick" Web applications by exploiting code or platform flaws is extremely important not only for functionality but for security as well. Core Files: (Fusebox)Files that create the foundation of a Fusebox application. They include (for Fusebox 4.x):
Cyclic Redundancy Code -- A small, integer value computed from a sequence of octets used to detect errors that result when the sequence of octets is transmitted from one machine to another. Typically, packet switching network hardware computes a CRC and appends it to a packet when transmitting. Upon reception, the hardware verifies the contents of the packet by recomputing the CRC and comparing to the value sent. Although more expensive to compute, a CRC detects more errors than a checksum that uses additive methods. Basically, it is an error-checking control technique that uses a polynomial algorithm to generate a 16-bit FCS (Frame Check Sequence) based on the content of the frame. The FCS is appended to the end of each frame and is matched by the receiver to determine whether an error has occurred. LLAP (LocalTalk Link Access Protocol) uses the standard CRC-CCITT algorithm: G(x) = x16 + x12 + x5 + 1. CRC-CCITT Calculation: The CRC-CCITT (cyclic-redundancy check Consultative Committee on International Telephone & Telegraph) algorithm, used to determine the FCS (Frame Check Sequence), uses the standard CRC-CCITT polynomial: G(x) = x16 + x12 + x5 + 1 The CRC-CCITT FCS value corresponding to a given packet is calculated based on the following polynomial division identity: M(x)/G(x) = Q(x) + R(x)/G(x) where: M(x) = binary polynomial (corresponding to the packet after complementing its first 16 bits) R(x) = remainder after dividing M(x) by the generating polynomial (its coefficients are the bits of the CRC) Q(x) = quotient after dividing M(x) by the generating polynomial (its coefficients are ignored when calculating the CRC) At the transmitter, the implementation of the CRC for the FCS field computes the CRC starting with the first bit of the destination node ID following the opening flag and stopping at the end of the data field. The FCS field is equal to the 1's complement of the transmitter's remainder. The same calculation is performed at the receiver; however, the FCS bytes themselves are included in the computation. The result of a correctly received transmission is then the binary constant 0001110100001111 (x15 ...x0). This constant is a characteristic of the divisor. In addition to the division of the data's binary value by the generation polynomial to yield the remainder for checking, the following manipulations occur:
If the receiver computation does not yield the binary constant 0001110100001111, the packet is discarded. CRM: (Harddrive)Customer Resource Management software. Crosstalk:The electrical interference between signals transmitted on wires. For example, overhearing another conversion during your phone call is an example of crosstalk. This interference will cause degradation in the transmitted data. Basically, this interference is generated when magnetic fields or current from nearby wires interrupt electrical currents in a wire. As electrical current travels through a wire, the current generates a magnetic field. Magnetic fields from wires that are close can interfere with the current in the other close wires, such that this interference will lead to signal reduction and/or jitter, or signal distortion. With Shielding and twisting wire pairs around each other help decrease crosstalk in wires. If twists are spaced properly, the magnetic fields in the wires cancel each other out. However, crosstalk can also be induced if the twists in a wire are badly spaced. Crosstalk comes in near and far-end varieties, known as NEXT and FEXT, respectively. FEXT (Far-end Crosstalk) is the interference in a wire at the receiving end of a signal sent on a different wire. NEXT (Near-end Crosstalk) is the interference ina s wire at the transmitting end ofa signal sent on a different wire. NEXT is the value generally measued when evaluating or testing cable. Current Graphical Systems:In the last dozen years a number of graphic systems have been introduced and are available in the marketplace. These systems are briefly introduced in the following paragraphs. The reader in need of detailed information concerning their design and operation is referred to their design documentation. Another source of information is Marcus (1992), who provides a comparative evaluation of the operational characteristics of several of those listed. Macintosh Introduced in 1984 by Apple Inc., it was the first mass-marketed, widely accepted graphic system providing the interactive style referred to as direct manipulation. Its success is attributed to its consistent and user-oriented interface. Its simplicity is in the result of what is called the desktop metaphor which makes it easy to learn. In which, this metaphor leads to intuition of the basic operation of the desktop design. Some feel this simplicity limits the flexibility available to the expert user. However, this is far from the truth. The Macintosh interface can be thought of as a finely balanced set of compromises. It relies heavily on a nested menu system, but the main menu is spread sideways so that it doesn't dominate the screen. The secondary menus are instantly available and pop in and out to conserve screen space. The Macintosh interface has been enhanced over the years. Moreover, the GUI is embedded into the operating system. This means that all applications that run on a Macintosh computer have a similar user interface. Once a user has become familiar with one application, he or she can learn new applications relatively easily. The success of the Macintosh GUI led heralded a new age of graphics-based applications and operating systems. The Windows interface copies many features from the Mac. There are many different Macintosh models, with varying degrees of speed and power. All models are available in many different configurations. All models since 1994 are based on the PowerPC microprocessor. The newest models (2002) are based on the new operating system known as Mac OS X. Mac OS X is a super-modern operating system that delivers the power of UNIX with the simplicity and elegance of the Macintosh. Engineered to take the Macintosh platform through the next decade, Mac OS X combines new and open standard technologies that make it the most stable, compatible and interoperable desktop operating system available. The Core OS includes Darwin. The Mach 3.0 kernel in Darwin gives Mac OS X its robust UNIX base. Networking -- plant the Mac in any environment -- Mac, Windows or UNIX. Internet Standards -- the Mac OS networking architecture supports all major protocols. Building Blocks of Tomorrow. Darwin is the rock-solid open-source foundation holding up the structure. On top of that, Mac-specific services provide top-notch multimedia integrated with Apple hardware. Frameworks are the method programmers use to manipulate these layers. You use Aqua or AppleScript to work with programs and the operating system. Mac OS X (pronounced "Mac OS Ten"), the latest incarnation of the Macintosh operating system, is a radical departure from previous versions. Not only is there a whole new look and feel (dubbed "Aqua"), there are huge differences under the hood. All the old, familiar Macintosh system software has been replaced with another operating system, called Unix. Unix is multiuser, multitasking operating system. Being multiuser means Mac OS X allows multiple users to share the same system, each having the ability to customize the desktop, create files that can be kept private from other users, and to make settings that will automatically be restored whenever that person uses the computer. Being multitasking means the computer can easily run many different applications at the same time, and that if one application crashes or hangs, the entire system doesn't need to be rebooted. NeXTStep Introduced in 1988 by NeXT Computer, it was the first to present a simulated three-dimensional appearance for its desktop components. Like the Macintosh, its simplicity and user-oriented interface is oriented toward inexperienced and nontechnical as well as the experienced and technical users. It provides a very good set of end-user customization tools. NeXTStep was purchased by Apple Computer. OPEN LOOK OPEN LOOK was developed as the standard operating environment for UNIX System V.4 by AT&T and Sun Microsystems. Providing more functionality that Macintosh or NeXTStep, it provided more power and flexibility for the expert user at the COST of increased learning requirements for the inexperienced user. It possesses many innovative appearance and "behavioral characteristics" in order to AVOID potential legal challenges, and it also provides an excellent functional specification and style guide. OPEN LOOK is used by Sun Microsystems workstations. DECwindows An interface for workstation software, it was announced in 1987. One of its goals was to achieve a consistent interface across operating systems, including VMS and UNIX, and across different input and screen configurations. A resulting product for achieving consistency is the XUI (X User Interface) style guide and toolkit (Digital Equipment Corporation, 1988). OSF/Motif A window-manager and user interface toolkit, it was developed by Digital Equipment Corporation and Hewlett-Packard for the Open Software Foundation (OSF). Its appearance and behavior are based upon OS/2 Presentation Manager. Customization is encouraged, and some stylistic guidance is provided through a style guide (Open Software Foundation, 1991). Like NeXTStep, it presents a simulated three-dimensional appearance. MS-DOS MS-DOS (Microsoft Disk Operating System) was the Microsoft-marketed version of the first widely installed operating system in perosnal computers. It was essentially the same operating system Bill Gates's young company developed for IBM as PC-DOS (Personal Computer DOS). Most users of either DOS system simply referred to their system as DOS. Like PC-DOS, MS-DOS was a nongraphical, line-oriented, command-driven operating system, with a relatively simple interface but not an overly "friendly" user interface. It was not capable of multitasking. Microsoft Windows 3.1 Originally created in 1985 as a graphics-oriented alternative to MS-DOS, it opened the door to graphics-oriented software on the PC. Initially limited by the design characteristics of DOS, it has been enhanced over the years. The user interface is not as easy as desired for inexperienced users, and its extensive use of keyboard equivalents was intended to ease the transition for experienced DOS users. OS/2 Presentation Manager Developed jointly by Microsoft and IBM in 1987, it was intended (but due to dissolution of business relationship between the two companies was dropped) as the graphics operating system replacement for MS-DOS. OS/2 Workplace Shell Developed by IBM when Microsoft and IBM dissolved their business relationship, OS/2 Workplace Shell is the GUI for OS/2 2.0 and beyond. Microsoft Windows 95 A much delayed OS replacement for the Windows 3.1, it is now the new mainstream version of Windows OS which was finally released in 1995. It incorporates a poesido true operating system and networking features. It also claims to possess a data or object orientation. With its many new features, Windows 95 was designed to eliminated a number of usability problems existing in Windows 3.1. Its general goals were to make it easier to learn for novices, more efficient and customizable for the experienced, and to reflect an object- or data-oriented approach. Microsoft Windows 98 Originally it was called Memphis, and then Windows 97, but Microsoft changed the name when it realized that it was going to miss its target 1997 release date. Windows 98 offers support for a number of new technologies, including FAT32, AGP, MMX, USB, DVD, and ACPI. Its most visible feature, though, is the Active Desktop, which integrates the Web browser (Internet Explorer) with the operating system. From the user's point of view, there is no difference between accessing a document residing locally on the user's hard disk or on a Web server halfway around the world. Microsoft Windows NT Microsoft's Windows NT (New Technology) is a 32 bit, preemptive, multitasking operating system with built in networking capabilities and security services. Windows NT is designed to be portable, and runs on CISC (Complex Instruction Set Computing), RISC (Reduced Instructions Set Computing), and symmetric multiprocessor computer architectures. Windows NT's modular design makes it easier to extend by adding new modules and also easier to port to other machines by isolating hardware dependent elements in separate modules. There are actually two versions of Windows NT: Windows NT Server, designed to act as a server in networks, and Windows NT Workstation for stand-alone or client workstations. Microsoft Windows 2000 Microsoft decided to rename the next release of the Windows NT line of operating systems -- formerly known as Windows NT 5.0 -- as Windows 2000. This operating system, with 30 million lines of code, took four years to complete and cost Microsoft more than $1 billion to develop. Windows 2000 Professional is a desktop operating system aimed at businesses of all sizes. Microsoft designed Windows 2000 Professional as the easiest to use Windows yet, with high-level security and significant enhancements for laptop users. The operating system is also designed to provide high reliability. The Microsoft Windows 2000 family of operating systems builds upon Microsoft Windows NT technology by adding many features and enhancements. Windows 2000 is more reliable, more scalable, and easier to deploy, manage, and use than previous versions of Windows. The Windows 2000 platform significantly reduces costs, enables a new generation of applications, and provides an organization with a solid infrastructure upon which to build their digital nervous system. The Windows 2000 platform consists of four operating systems. Once you understand the capabilities of each of the Windows 2000 operating systems, you will be able to select the bet product to meet the current and future needs of your organization. The table below describes the operating systems that are included in the Windows 2000 platform.
Cut Through Switching: A switching method for Ethernet networks. The switch reads a destination address and immediately starts forwarding packets, without first checking the integrity of each packet. This reduces latency. There are two switching strategies for implementing cut-through switches:
Compare with Store and Forward Swtching. Cycle, Periodic Analog Signal:One complete repetition of a periodic analog signal. A cycle goes form a high point (peak) in the signal's level to a low point (through) and back to the peak. The cycles per second value defines the frequency of a periodic signal. Frequency is measured in hertz (Hz). For example, a 50Hz signal travels at 50 cycles per second. Cycle, FDDI II:In an FDDI (Fiber Distributed Data Interface) II network operating in hybrid mode, a cycle is a 12,500 bit protocol data unit (PDU), or packet, that provides the basic framing for FDDI transmission. The cycle is repeated 8,000 times per second, which yields 100 megabits per second (Mbps) of bandwidth for the network. Cyclic Redundancy Checksum (CRC) ProblemThe following is the worked out problem to show how a CRC is determined for the message "101101100101" using a generator polynomial of "1000011" = x6 + x + 1. The fundamental method used is to add 6 zeros to the message (1 less than the length of the generator polynomial) and then continually do an exclusive-or (XOR) operation.
101101100101 000000 <- the message with appended zeros
1000011 <- the generator polynomial
-------
1100000 <- the result, with 2 digits brought down...
1000011
------- <- ... and the above process repeats...
1000111
1000011
-------
10001 00 <- the gap is just for consistency
10000 11
--------
1 110000
1 000011
--------
110011 <- we can't go any further!
So, the answer is "110011" because the CRC must be 6 bits long as decided above. These six bits are attached to the original message and transmitted. At the other end, the above process is applied to the message with its CRC and if all is well the result should be 0. Have tryed below, repeating the above with "101101100101 110011" and the same generator polynomial and get "0". Checking CRC value:
101101100101 110011 <- the message with appended CRC
1000011 <- the generator polynomial
-------
1100000 <- the result, with 2 digits brought down...
1000011
------- <- ... and the above process repeats...
1000111
1000011
-------
10001 11 <- the gap is just for consistency
10000 11
--------
1 000011
1 000011
--------
0 <- we can't go any further, it checks!
Checking CRC value, with errors at postions 0,10,12:
1111101100100 110011 <- the message with errors and appended CRC
1000011 <- the generator polynomial
-------
1111101 <- the result, with 2 digits brought down...
1000011
------- <- ... and the above process repeats...
1111100
1000011
-------
1111110
1000011
-------
1111011
1000011
--------
1110000
1000011
-------
1100110
1000011
-------
100101 1 <- the gap is just for consistency
100001 1
--------
100 0100
100 0011
--------
11111 <- we can't go any further, check fails
Checking CRC value, with errors at postions 2,3,8:
101001101001 110011 <- the message with errors and appended CRC
1000011 <- the generator polynomial
-------
1000001 <- the result, with 2 digits brought down...
1000011
------- <- ... and the above process repeats...
10001 11 <- the gap is just for consistency
10000 11
--------
1 000011
1 000011
--------
0 <- we can't go any further, it checks, however the
error check fails because we had errors!
| |||||||||||||||||
| Back | Home | Top | Feedback | Site Search |
 E-Mail Me |
This site is brought to you by This page was last updated on
09/18/2005 |
This Page has been accessed "9783" times.