| RDB PRIME! Engineering |
|
|
|
|
|
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| It is 17:40 PST on Monday 10/06/2025 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
Facility .. to .. Function Management Layer (FML)
Facility: In telephone communications, a transmission link between two locations, or stations. In an X.25 packet, a facility is a field through which users can request special services from the network. Any set of transmission paths that can be used to transport voice or data. Facilities can range from a cable to a carrier system or a microwave radio system. Facility Bypass:In telecommunications, a communication strategy that bypasses the telephone company's central office. For example, wirless transmissins might use facility bypass. Facility Data Link (FDL):In an ESF digital transmission format, a 4 kilobit per second (kbps) communications link between the sender's station and the telephone company's monitors. This 4 kbps band is created by taking half of the 24 framing bits in an ESF (Extended Sperfarme) and using them for the link. Also see Extended Superframe). Facsimile:A system for scanning a document, encoding it, transmitting it over a telecommunications circuit, and reproducing it in its original form at the receiving end. Fading:In electrical or wireless signaling, fading is the decrease in the signal's strength because of any of the following:
Fading is sometimes referred to as just fade, as in fade margin. The fade margin refers to the amount of signal (in decibels) that can be lost before the signal becomes unintelligible. Fail-Safe System:A computer system that is designed to keep operating, without losing data, when part of the system seriously malfunctions or fails completely. Fail-Soft System:A computer system that is designed to fail gracefully, with the minimum amount of data or program destruction, when part of the system malfunctions. Fail-soft systems close down nonessential functions and operate at a reduced capacity until the problem has been resolved. Fake Root:In Novell's NetWare versions 3.x and 4.x, a fake root is a drive mapping to a subdirectory that makes the subdirectory appear to be the root directory. A fake root allows you to install programs into subdirectories, even though they insist on executing in the root directory. With the programs in a subdirectory, administrators can be more specific about where they allow users to have rights, and avoid granting rights at the true root of the volume. Fake roots are not allowed in all environments. For example, fake roots cannot be used with OS/2 clients. When a fake root is used, there are also restrictions on how certain commands work and on how certain actions -- for example, returning to the original (non-fake) root -- must be performed. Also see NetWare. Fast Ethernet:Fast ethernet has its roots with Grand Junction Networks, a company formed by the original developer of Ethernet. Fast Ethernet came about as a means to leverage the wiring infrastructure in place at over 90 percent of all LAN installations for 100 Mbps support. Fast Ethernet is 100 Mbps data rate over twisted wire (100BASE-T). The specification of 100BASE-T is defined in the IEEE 802.3u standards. The IEEE 802.3u 100BASE-T standard requires a star-wired topology. The IEEE 802.3u specification supports unshielded twisted pair (UTP) and fiber optic. Fast Ethernet CSMA/CD:A main objective in the development of the 100BASE-T standard was to keep the IEEE 802.3 MAC (Medium Access Control) frame format and parameters intact as much as possible. This was accomplished with only the InterFrameGap (IFG) time changed from 9.6 to 0.96 microseconds as a minimum due to the increased data rate of Fast Ethernet (10 times faster than 10 Mbps Ethernet). Though stations on 100 Mbps Ethernet are not on a bus topology they still implement the listen-before-sending CSMA/CD (Carrier Sense Multiple Access/Carrier Detect) protocol prior to sending. The CSMA/CD protocol is implemented on 100BASE-T over four different types of physical layer specifications. These are 100BASE-TX, 100BASE-T4, 100BASE-T2, and 100BASE-FX. Federal Communications Commission (FCC):The Federal Communications Commission (FCC) is not a standards organization, but it has served as the regulatory authority for radio, television, wire, and cable communications within the United States. The FCC has the charter to retain regulatory control over interstate and international commerce concerning communications. The FCC strives for competitiveness in these markets, which relates to the public benefits of marketplace fairness, up-to-date and quality communications systems, and a broad range of communications offerings for the consumer. The FCC also has responsibilities for reviewing the rate and service change applications for telegraph and telephone companies, reviewing the technical specifications of communications hardware, and setting reasonable common carrier rates of return. These goals extend to the regional holding companies (RHCs) and the interexchange carries (IXCs), and technical and regulatory policy issues by which they are affected. The FCC also publishes guidelines to govern the operation of communications and other electrical equipment in the United States. Perhaps the best-known FCC regulations are those that define and govern class A and class B devices, and those that allocate the electromagnetic spectrum. The device (computers, printers, i.e., all commercial and private electronic products sold in the US) certifications are based on the amount of radio frequency interference (RFI) the devices may cause for other devices in the vicinity. Class A certification is less stringent, and is assigned to equipment for use in business contexts. The more stringent class B certification applies to devices that are used in the home. The FCC also allocates portions of the electromagnetic spectrum for particular uses, such as the following:
In a fiber-optic connection, a component that serves to keep the optical core and cladding aligned and immobile. The fiber cladding may be glued to the ferrule with epoxy. Ferrules may be made of ceramic (the most reliable), plastic, or stainless steel. Fiber Distributed Data Interface (FDDI):FDDI is a proposed ANSI standard specification (X3T9.5) for a network architecture that is designed to use fiber-optic lines at very high speeds. An FDDI network has the following charcteristics:
Apple's implementation of FDDI (Fiber Distributed Data Interface) protocols and drivers for use in an AppleTalk network. Also see EtherTalk, LocalTalk, and/or TokenTalk. Fiber-Optic Cable:Fiber-optic cable, also known as optical fiber, provides a medium for signals using light rather than electrical current. Cables of this type differ in their physical dimensions and composition and in the wavelength(s) of light with which the cable transmits. The table "Context and Properties of Fiber-Optic Cable" sumarizes the features of this type of cable. CONTEXT AND PROPERTIES OF FIBER-OPTIC CABLE:
Because fiber-optic communication uses light signals, transmissions are not subject to electromagnetic interference. This, and the fact that a light signal encounters little resistance on its path (relative to an electrical signal traveling along a copper wire), means that fiber-optic cable can be used for much longer distances before the signal must be cleaned and boosted. Some fiber-optic segments can be several kilometers long before a repeater is needed. If fact, scientists have sent signals over fiber-optic lines for thousands of kilometers without any signal boosters. In 1990, researchers sent a 1 gigabit per second (Gbps) signal almost 8,000 kilometers (about 5,000 miles) without a boost! In principle, data transmission using fiber optics is many times faster than with electrical methods. Speeds of over 10 Gbps are possible with fiber-optic cable. In practice, however, this advantage is still more promise than reality, because the cable is waiting for the transmission and reception technology to catch up. Nevertheless, fiber-optic connections deliver more reliable transmissions over greater distances, although at a somewhat greater cost. Fiber-optic cables cover a considerable price and performance range. Fiber Optic Multiplexer:A fiber optic multiplexer takes multiple channels of data, with each channel transmitting at 64,000 bits per channel, and multiplexes the channels onto a 14 million bits per second fiber optic line. It is similar in operation to a time division multiplexer (TDM, see time division multiplexer), but operates at much higher speeds. File Server:A computer specifically intended for storing files and applications that others can share over the network. The computer being used as the file server might not be able to be used for other common workstation tasks. Workstations used for a single purpose like a file server are called dedicated devices because they are dedicated to a single function. Often a dedicated file server is kept away from work areas for security reasons and prevent accidental or malicious use. However, not all file servers must be dedicated. Some networking software allows any workstation to handle file server tasks and still function as workstation, such as the Mac OS 7.1 via AppleShare. In general a file server is simply a computer with one or more large-capacity hard disk drives. Normally, it is composed of a minicomputer or a fast microcomputer. This is done since many users will be accessing the server at the same time, requiring a high performance machine with fast hard disks. File Transfer, Access, and Management (FTAM):In the OSI Reference Model, an application layer protocol and service for remote file access, FTAM enables an application to read, write, or otherwise manage files on a remote machine. File Transfer Protocol (FTP):In the TCP/IP (Transmission Control Protocol/Internet Protocol) (or Internet) protocol suite, a file transfer protocol. FTP is an application layer protocol that uses the services of the TCP protocol at the transport layer to move the files. Anonymous FTP is an example of this protocol. Anonymous FTP is used to download files form public directories. This provides a generic download mechanism. To use anonymous FTP, the user proceeds as follows:
As Anonymous, the user will be allowed access to the directory containing the file or files desired. The system will send the requested files to the address specified as the password. Basically FTP moves data between any two hosts independent of operating system and file type or character representation. Data files on an IBM mainframe, using EBCDIC character set, can be transferred to a Windows PC, Macintosh, or UNIX workstation as ASCII files, without any special treatment or need for conversion. File management tools are provided in the basic FTP implementation, but files on a remote system must be transferred before they can be used in any way on the local system. So, although an FTP client can be used to display directory listings, including file name, size, type, and creation date, the contents of that file can't be examined until it has been transferred to the local host. As with all TCP/IP applications, a set of commands are defined by the FTP protocol specifications. Any FTP client must offer a minimal selection of these commands, and any FTP server must be able to respond to any of the supported commands. If you are familiar with FTP commands on one system, you can use the same commands on any other system that implements FTP. A typical command-line session will be the same on any system running an FTP client program though there may be slight cosmetic differences, for instance, the command line prompt may be different. Increasingly, personal computer TCP/IP software vendors have been moving from implementing FTP as a command-line program to implementing it as a graphical user interface (GUI) program, partcularly under Windows, OS/2, and the Macintosh operating systems. Although the user interface eliminates command lines and the standard FTP commands from the user session, they are implemented underneath the graphics. A GUI FTP implementation may support drag and drop copying, but the FTP application program is still sending the standard FTP copy commands to the FTP server while displaying the results graphically. Reflecting this is the trend by vendors of renaming their GUI FTP client something else, like Novell's Rapid Filer, and SPRY's Network File Manager, or for the Macintosh the program Fetch. Floating Point Unit (FPU):A math coprocessor chip that specializes in doing floating-point arithmetic. Examples include the 80x87 family of processors from Intel, as well as third-party FPUs, such as those from Cyrix and AMD. Another example is Motorla's 68040 family of CPUs (computer processing units) that have the FPU as part of their architecture. Flops:Floating point operations per second. The term "floating point" refers to that format of numbers that is most commonly used for scientific calculation. Flops is used as a measure of a computing system's speed of performing basic arithmetic operations such as adding, subtracting, multiplying, or dividing two numbers. FireWall:This is a computer and software combination that isolates your internal network from the Internet. Whenever someone inside your organization (on your internal network) wants to browse a Web page, their browser goes to the firewall, which lets them "through" to the Internet. Likewise, someone on the Internet outside your network can get "in" to read Web pages or download files only if the firewall lets them, usually via a user name and password. Typically, you'd put a WEB and file servers outside the firewall so that, if they did get hacked, the damage to your internal network would be minimal. This way, interlopers can't rummage around inside your network even if they find a way in through your servers. Many recent computer security discussions refer to firewall systems. The term "firewall" implies protection from danger, and just as the firewall in your car protects the passengers' compartment from the car's engine, a firewall computer system protects your network from the outside world. A firewall computer provides strict access control between your systems and the outside world. The concept of a firewall is quite simple. A firewall system replaces an IP router with a multi-homed host that does not forward packets. By not forwarding IP packets between networks, firewalls effectively "sever" the connection between the networks (the role that IP routers, also called gateways, play in gluing the Internet together). To provide the network behind the firwall with some level of network connectivity, the firwall performs certain unique functions discussed below. The figure below "Firewalls versus Routers" shows a comparison between an IP router and a firewall. A router handles packets up through the IP layer. The router forwards each packet based on the packet's destination address, and the route to that destination indicated in the routing table. A host, on the other hand, does not forward packets, and the firewall system is just a special type of multi-homed host. See the IPFORWARDING parameter for information on how to prevent a multi-homed host from forwarding packets. Just like any host, the firewall accepts packets that are adressed to it, and processes those packets through the (OSI) Application Layer. The firewall ignores packets that are not addressed to it. 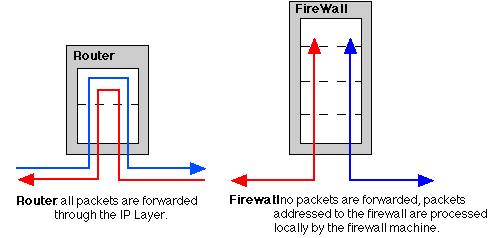
This definition of a firewall, as a device completely distinct from an IP router, is not universally accepted. Some people refer to routers with special security features as firewalls, but this is really just a matter of semantics. In this discussion, routers with special security features are called secure routers or secure gateways. Firewalls, on the other hand, are not routers because they do not forward packets, even when they are used in place of routers. Because firewalls are used in place of routers, they are usually thought of as a way to separate an internal network from the external world. However, isolating an entire network behind a firewall may not be required. Even at sites that need a firewall, most workstations and desktop computers may not contain information or applications that need this level of protection. Frequently, only a limited set of computers contain truly sensitive data or processes critical to the operation of the organization. One way to limit the impact of a firewall on the operation of a network is to use an internal firewall that isolates selected critical systems to operate in a normal manner. The figure below "Internal and External Firewalls" illustrates networks using both internal and external firewalls. The difficulty of identifying all sensitive systems, and the fear of making a mistake that could compromise critical information, causes may security-conscous sites to prefer an external firewall, or even a combination of internal and external firewalls. However, if sensitive systems can be identified and isolated, the majority of users benefit from a more user friendly network because the entire network is not isolated behind an external firewall. 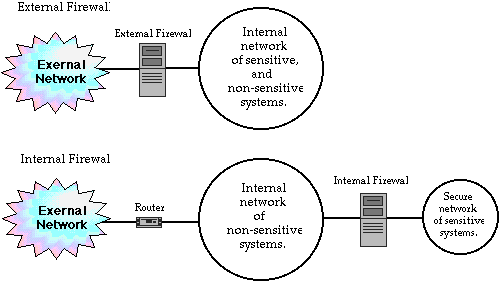
Functions of the Firewall With a firewall in place, an intruder cannot mount a direct attack on any of the systems behind the firewall. Packets destined for hosts behind the firewall are simply not delivered. The intruder must instead mount an attack directly against the firewall machine. Because the firewall machine can be the target of break-in attacks, it employs very strict security guidelines. But because there is only one firewall machine versus many machines on the local network, it is easier to enforce strict security on the firewall system. The disadvantage of a firewall system is obvious. In the same manner that it restricts access from the outside into the local network, it restricts access from the local network to the outside world. To minimize the inconvenience caused by the firewall, the system must do many more things that a router does. The firewall must provide:
Only the minimal services listed above should be provided on a firewall system. Other common network services (NIS, NFS, rsh, rcp, finger, etc.) should generally not be provided. Services are limited to decrease the number of holes through which an intruder/hacker can gain access. On firewall systems, security is more important than service. ftp service and remote terminal service are the biggest problems for the firewall machine. To maintain a high level of security, user accounts are discouraged on the firwall machine, but at the same time users must log in to the firewall system to have access to ftp and remote terminal services. This problem is usually handled by creating a special user account for ftp, and one for telnet, that are shared by all internal users. Group accounts are generally viewed as security problems, but if these accounts are carefully designed and properly restricted, they can be reasonably secure. Because a firewall must be constructed with great care to be effictive, and because there are many configuration variables for setting up a firewall machine, vendors are beginning to offer special firewall software for their systems. Some vendors sell special-purpose machines designed specifically for use as firewall systems. Before setting up your own firewall, investigate the options available from your hardware vendor. Firewall systems are useful to some sites that have special security needs, but for many other sites they are not appropriate. The restrictions that they place on individual users are not acceptable to many organizations, and the restrictions can drive independent-minded users to find other ways to handle their communications needs. Flow Control Methods:Flow control (also called handshaking) is an asynchronous communication protocol that is used between communicating devices to regulate the flow of a stream of data. If one station has received more information than it can hold in its buffers or process at one time, it signals the sender to pause the transmission until it can catch up. Flow control signaling can be performed in hardware (out-band signaling) or in software (in-band signaling). Hardware flow control takes place between two systems that are directly connected together with a multiline cable. One or two of the lines are used for data transfer. Other lines are used for signaling. For example, in the request to send/clear to send (RTS/CTS) signaling method, a terminal device signals that it can send data by turning on its RTS line. The other device turns on its CTS line as a response. To control the flow, the receiver can turn off its CTS line at any time. Software flow control assumes that devices are communicating on a single-wire channel, such as a telephone line connected with modems. In this case, XON/XOFF flow control can be used. An XON character indicates that a device can receive data. An XOFF character stops the flow of data until an XON is sent. Forwarding:In a network bridge, router, or gateway, or in a packet-switching node, forwarding is the process of passing a packet or message on to an intermediate or final destination. This is in contrast to filtering, in which a packet is discarded. The basis for the filtering or forwarding can be address or protocols. Ordinarily, a bridge or another forwarding device does the follow:
In on-the-fly forwarding, a device begins forwarding the packet as soon as the device determines that this is the appropriate action. This means that the packet can be on its way to a new destination while still being read by the bridge. Fourier Analysis:Fourier Analysis studies the representation of continuous functions by a superposition of harmonic (that is, sine and cosine) functions. Fourier analysis was originally developed as an engineering tool to study repetitious phenomena such as the vibration of a stringed musical instrument or an airplane wing during flight. It is also used in technical analysis to detect cyclical patterns within prices. Fourier analysis, a pervasive and versatile tool, is used in many fields of science as a mathematical or physical tool to alter a problem into one that can be more easily solved. Some scientists think of Fourier analysis as a physical phenomenon, not simply as a mathematical tool. In some branches of science, the Fourier transform of one function may yield another physical function. For example, the Fourier transform decomposes or separates a waveform or function of time into sinusoids of different frequency, which sum to the original waveform. It identifies and distinguishes the different frequency sinusoids and their respective amplitudes. With the exception of some mathematical curiosities, any periodic signal of period T can be expanded into a trigonometric series of sine and cosine functions (a Fourier series). If a function or waveform is not periodic, then the Fourier transform of the function will be a continuous function of frequency. There are functions for which the Fourier transform does not exist; however, most physical functions have a Fourier transform, especially if the transform represents a physical quantity. Other functions can be treated with Fourier analysis as limiting cases. Many of the common theoretical functions are actually limiting cases in Fourier analysis. We can view the discrete Fourier transform as a function that maps a sequence over time {f(t )} to another sequence over (angular) frequency {F(w)}. (NOTE: We have written w for the angular frequency instead of Greek omega because all browser fonts may not recognize the Greek letter.) The sequence {f(t)} represents a sampling of a signal's distribution as a function of time. The sequence {F(w)} represents the distribution of Fourier coefficients as a function of frequency. We can use {F(w)} to compute the sinusoidal components of the sampled signal. From the non-zero elements of {F(w)} we can determine the frequency of the terms generating the signal, where frequency means the number of cycles the term completes in unit time (that is, one second). Non-zero real components correspond to cosine functions; non-zero imaginary components correspond to sine functions. The discrete Fourier transform has many applications in science and engineering. The complete Fourier analysis concept is called spectral analysis. Fast Fourier Transform (FFT) is an abbreviated calculation that can be computed in a fraction of the time required for an ordinary Fourier transform. FFT sacrifices phase relationships and concentrates only on frequency (or the reciprocal of cycle duration) and amplitude. The benefit of FFT is its ability to extract the predominant frequencies from a series of data. FFTs are based on the principle that any finite, time-ordered set of data can be approximated by decomposing the data into a set of sine waves. Each sine wave has a specific frequency, amplitude, and phase relationship to the other sine waves. Fragmentation: (Network)In order to transmit packets over any type of network, IP must be capable of adopting the sizes of its datagrams to each network. Thus, for example, CCITT (Comite Consultatif International Telephonqiue et Telegraphique) X.25 packets should not be larger than 128 bytes, Token Ring packets which can be as large as 15000 bytes, while an Ethernet packet may transport up 1526 bytes of data. To achieve efficient transport between the two different networks, it is not sufficient that the transport protocols, such as TCP (Transmission Control Protocol) or UDP (User Datagram Protocol), are themselves only able to generate small packets. Since a packet, en route from the source to the destination, may, in certain cases, pass through several different networks with different maximum packet sizes and since, moreover, this route may vary from packet to packet within a TCP connection, a flexible procedure must be applied: Thus fragmentation. Fragmentation means that the IP of each node in the network should be capable of dividing a received packet, in order to transmit it over a subnetwork to the next node or host. Every destination IP should be capable of reassembling fragmented messages. Fragmentation and Allocation Schemas: (DDBMS)The fragmentation schema is a description of how the data is to be logically partitioned. The allocation schema is a description of where the data is to be located, taking account of any replication. Frame:Literally, a packet as it is transmitted across a serial line. The term derives from character oriented protocols that added special start-of-frame and end-of-frame characters when transmitting packets. It is also referred to the actual objects that a physical network transmits, even if the network does not use traditional framing. X.25 networks use the term to specifically refer to the format of data transferred between a host and the a packet switch. Put another way, it is a series of bytes of data encapsulated with a header. The data link layer (see data link layer) sends frames back and forth. The term frame is often used interchangeably with the term packet. See packet. But basically, it is a group of bits forming a distinct transmission unit that is sent between data-link-layer entities. Each frame contains its own control information for addressing and error checking. The first several bits in a frame form a header that contains address and other control information, followed by the data (or message) being sent, and the ending with a check sequence for error detection. Frame Check Sequence (FCS):A 16-bit sequence used for error checking that occurs at the end of a each frame. In a LocalTalk implementation, the standard CRC-CCITT algorithm is used to compute the FCS. It is computed as a function of the contents of the destination node ID, source node ID, LLAP type, and data fields. Frame Relay:Frame Relay provides services similar to X.25, but is faster and more efficient. Frame Relay assumes that the telecommunications network is relatively error-free and does not require the extensive error checking and packet acknowledgment features of X.25. Frame Relay is an excellent choice for organizations that need any-to-any connections on an as-needed basis. A customer connection into a public Frame Relay network takes the form of a switched or dedicated leased line like T1. Customer traffic is forwarded through this line to the Frame Relay provider and switched across the network. Framing:The specification of how electronic signaling on a T-1 circuit is divided into 24 DS-0 channels, plus how the communication on the T-1 circuit is controlled. Two options for framing exist: D4 or Extended Superframe Format (ESF). ESF is the standard. Frequency Division Multiplexing (FDM):In FDM, a modem and a frequency division multiplier are used to break down the frequency of available bandwidths of a voice-grade circuit, dividing it into multiple smaller bandwidths. The bandwidth is a measure of the amount of data that can be transmitted per unit of time. See bandwidth. Assume that a telephone circuit has a band width of 3100 Hz, and a line capable of carrying 1200 bits per second (bps). Suppose that instead of running a terminal at 1200 bps, it is desired to run three terminal at 300 bps. If three terminals are going to use the same communication line, then some type of separator is required in order to avoid crosstalk (interference of signals from one to another, see crosstalk). This separator is called a guardband. For transmission at 300bps the standard separation is 480 Hz. Therefore, in the above situation, two guardbands of 480 Hz each are required. Since the guardbands now occupy 960 Hz, and the original line had a bandwidth of 3100 Hz, then the frequency left for the 300 bps transmission is 2140 Hz. If three terminals are required, then 2140 Hz divided by three gives a frequency of 713 Hz to be used per channel. With FDM it is not necessary for all lines to terminate at a single location. Using multidrop techniques, the terminals can be stationed in different locations within a building or a city. *Front End Processor (FEP):Front end processors are often employed at the host end of a communication circuit to perform control and processing functions required for the proper operation of a data communication network. The front end processor provides an interface to the communication circuits. It relieves the host computer of its communication duties, which allows the host to perform the data processing function more effectively. The typical duties of the front end processor are message processing and message switching. In message processing, it interprets incoming messages to determine the type of information requested. Then it retrieves the information from an on-line storage unit, and sends it back to the inquiring terminal without involving the host system. In message switching, the front end processor switches incoming messages to other terminals or systems on a network. It can also store messages and forward them at a later time. Functions of the Front End ProcessorThe functions of the front end processor includes the following when attached to a LAN:
A communication setup in which transmissions can travel in both directions at the same time. This is in contrast to simplex and half-duplex connections. Function Management Layer (FML):The topmost layer in IBM's SNA. An enduser deals directly with this layer which, in turn, deals with the data-flow control layer. Also see Systems Network Architecture (SNA). Functional Decomposition: (UML)An approach to systems development in which the larger system is broken down into smaller parts. Those parts may then be broken down into even smaller parts, and so on. Each part of the system that is so decomposed is an aggregate of its smaller parts.
| ||||||||||
| Back | Home | Top | Feedback | Site Search |
 E-Mail Me |
This site is brought to you by This page was last updated on
09/18/2005 |
This Page has been accessed "6412" times.