| RDB PRIME! Engineering |
|
|
|
|
|
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| It is 16:04 PST on Monday 10/06/2025 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
T, or Tera .. to .. Twisted-Pair Cable
Tablespace: (Database) A construct representing an amount of storage space that is to be allocated to tables, indexes, and so on. Tagged Value: (UML)Allows additional information about a standard UML element to be specified. T, or Tera:A prefix denoting 1012 or a trillion; for example, terabits, teraflops. T-1:T-1 is a term used to described time division multiplexed (TDM, see time division multiplexing) data carrier T-span service, including a cable and its hardware, used to transmit digital signals at an aggregate rate of 1.544 Mbps. T-1 can transmit a large volume of information in data, video, or voice from across great distances at high speed. It can do all this at a potentially lower cost than that provided by traditional analog service. A T-1 line consists of one four-wire circuit providing 24 separate 64-Kbps logical (digital) channels. Thus, T-1, T-2, T-3, T-4 -- are abbreviations for the various levels of digital bandwidth capacity of a T-carrier. They are used to indicate the speed at which data can travel over a network wire, measured in megabits per second: 1.5, 6.3, 44.7, and 274.2, respectively. T-1 Multiplexer:A T-1 multiplexer is a special type of multiplexer combined with a high capacity data service unit that manages the ends of a T-1 link. A T-1 link is a communication link that transmits a 1.544 million bits per second. T-1 circuits are normally subdivided into 24,48, or 96 voice-grade circuits. TCP:Transmission Control Protocol--The TCP/IP standard transport level protocol that provides the reliable, full duplex, stream service on which many application protocols depend. TCP allows a process on one machine to send a stream of data to a process on another. It is connection-oriented in the sense that before transmitting data, participants must establish a connection. Software implementing TCP usually resides in the operating system and uses the IP protocol to transmit information across the underlying internet. It is possible to terminate (shut down) one direction of flow across a TCP connection, leaving a one-way (simplex) connection. The entire protocol suite is often referred to as TCP/IP because TCP and IP are the two most fundamental protocols. At the transport layer are two major, and very different, transport protocols: TCP and UDP. Each supports applications with different requirements and expectations as to performance and reliability of data transmission. Although UDP supports "request/reply" transactions with no added reliability or guarantee of delivery, TCP offers a connection-oriented, reliable, and guaranteed-delivery service to applications that need a link that behaves like a circuit between two hosts. Also at the transport layer, headers are added to parcels of data to create TCP segments or UDP datagrams. The headers include information linking the enclosed data to specific processes; the data within, including the application headers, is largely ignored. TCP uses the combined specifier of internetwork address and port number, called a socket, to uniquely identify internetwork virtual circuits. With a socket on one host, defining the host itself (its internetwork address) and the program running on that host, combined with the same information for the other host, a unique network link can be defined. For example, a link between Host A, using Client Application X, and Host B, using Server Application Y, is defined by the internetworking addresses of the two hosts (Host A-Host B) and the port numbers of the applications (Client X-Server Y). TCP/IP (Transmission Control Protocol/Internet Protocol):Is the official name of the TCP/IP suite of protocols that let many networks interconnect. TCP/IP is the standard for internetwork communication established in the U.S. Department of Defense network known as ARPAnet. ARPA, also called DARPA, stands for the Advanced Research Projects Agency. ARPAnet is the research and development arm of the Department of Defense. TCP/IP is rapidly becoming a de facto standard for network interconnections for universities and research organizations. It has been associated with Unix networks because various companies selling Unix devices have built the TCP/IP protocols into the devices. Teardrop Attacks (Windows 2000):A Teardrop attack is executed using a program such as teardrop.c, that causes fragmentation similar to that seen in a Ping-of-Death attack. A teardrop attack takes advantage of a weakness in the reassembly process and can cause a system to hang or crash. Tele-nanoManipulator:A system enabling scientists to see, touch, and manipulate nanometer-scale objects, such as viruses, using remote microscopes over high-speed networks. TELNET:An upper layer TCP/IP protocol that provides virtual terminal services and allows users to log onto remote nodes. TELNET is specified in RFC 854 (Postel and Reynolds, 1983). It is intended to provide access, in the form of a terminal session (also called remote login or virtual terminal), to a computer connected to the network. In UNIX systems, the telnet command is used on the client side, while on the server side (the computer called over telnet) there is a so-called daemon or server known as telnetd. The TELNET service is attached to TCP port 23. TELNET is the login and terminal emulation program for Transmission Control Protocol/Internet Protocol (TCP/IP) networks such as the Internet. It was originally developed for ARPANET but is now mainly used in Internet sessions. Its primary function is to allow users to log into remote host systems. Originally, TELNET was a simple terminal program that sent all user input to the remote host for processing. Newer versions perform more processing locally, thus providing better response and reducing the amount of information transferred over the link to the remote host. TELNET is a client-server process in which the user invokes the TELNET application on the local system and sets up a link to a TELNET process running on a remote host. The user issues requests at the keyboard that are passed to the TELNET process running on a remote host. The user issues request at the keyboard that are passed to the TELNET server on the remote host. Through this process, users can initiate programs on the remote host and run those programs from their own systems as if they were attached directly to the remote host. Most processes run on the remote host. It receives requests from the user's system and processes them in its workspace, thus reducing traffic over the link. Terminator:A device attached to the end of a cable to prevent unwanted signals from being transmitted on the line or link ( i.e., noise). A terminator resistance matches the characteristic impedance of the line so that signals arriving at the end of the cable do not find an impedance discontinuity and are thus prevented from being reflected back to the transmitted source as unwanted noise. Testing Equipment and Techniques:The primary tools for network testing include cable testers and protocol analysis products. Cables testers are used to test or certify the physical cable plant, while protocol analyzers operate higher up in the protocol stack. A protocol analyzer can look at packets and determine which stations are generating traffic, monitor where errors are occurring, and watch for unusual events on the network such as peaks in traffic or resource usage. Network Cable Testers A common source of problems on a network is the cable. There are a number of devices you can use to test cable. Some are quite affordable and should be part of any network manager's toolkit. More expensive equipment can be rented, or you can rely on the services of consultants and professional cable installers. However, a new breed of cable testers is now available that includes a whole range of testing features, including protocol analysis, for several thousand dollars. Most are the size of portable phones. Some cable testing is performed simply to test existing cable or to certify that a cable installation follows customer, vendor, or industry standards for signal-to-noise ratios, performance, and integrity. Cable testers should test for the following:
If you don't have a specific cable-testing device, a simple voltage meter can serve as a tool for testing continuity. You set the meter to its ohm or resistance setting and measure through the center wire and then through the ground, or use an alligator clip to form a loop-back at one end of the cable. If the cable is already installed, you can still measure continuity. For coaxial cable, place a terminating resistor at one end of the cable, then touch the ground with one lead and the center wire with the other. For twisted-pair cable, use an alligator clip to connect the wire pair at one end, then test the other end. Cable Tracers You trace a cable to determine its path in a wall or ceiling, or its source and destination. A cable tracer is useful if you need to determine the destination of one wire in a bundle of wires. A tone generator is attached to one end of the cable and an amplifier is then used to listen for the tone at the other end, which is typically a punchdown block for twisted-pair cable. The amplifier indicates when it is near the wire that is producing the signal. A popular product is the Microtest Tracer. With it, you can locate any coaxial, twisted-pair, or other type of wire hidden inside hidden inside a floor, wall, or ceiling. The Tracer's sending unit is connected to the wire or cable, and then its pocket-size receiving unit is run over the areas where you suspect the wire runs. When the Tracer's receiving unit passes over the wire, and alarm sounds; the alarm grows stronger as you get closer to the wire. Time Domain Reflectometers (TDRs) A TDR determines the locations of breaks and shorts in cables. It sends a high-frequency pulse down the length of the cable and then measures the time it takes for the reflection of the signal to return. Reflections occur at shorts and breaks, and the time and amplitude of the reflection indicates the distance to the problem. In addition, the polarity indicates whether the problem is a short or an open connection. TDRs are now available for under $1,000 from vendors such as Black Box. Note that optical TDRs are also available for testing fiber-optic cable installations. The Microtest Cable Scanner (approximately $1,500) is a stand-alone, hand-held TDR, and can be purchased from Microtest. It has a 32-character display that reports fault problems in plain English, such as "Short at 306 ft". The Cable Scanner can print a hard copy to any serial printer and save test results in memory for later review. You can test Ethernet, ARCNET, and token ring networks that use coaxial or twisted-pair cable. The Cable Scanner also provides real-time monitoring of a local area network's activity to help determine when a bridge or repeater might need to be added. You can attach the Cable Scanner to an oscilloscope to analyze waveforms. The Tracer product described earlier is included with the Cable Scanner. Protocol Analyzers As a general rule, as a network grows, its performance drops. Of course, you can spend more money to upgrade the network. The practical alternative is to tweak settings and look for bottlenecks. You need to be an the lookout for improperly configured devices or overworked servers. You should also watch for excess wide area network (WAN) traffic. Cable testers and local area network (LAN) analysis products can help you determine the source of problems. If you have a LAN with over 50 nodes, such products are easily justified, especially if the nodes are scattered over a large area. They let you analyze the network from your office and locate potential problem areas. Many of the tasks you can do with a protocol analyzer are listed here:
Of course, this is only a small sampling of protocol analyzer activities. Products differ in their capabilities, so you should check with the manufacturer and read product evaluations in trade journals and information that can be obtained from the World Wide Web. Several of the manufactures now have web sites where you can go and read about there products and even work with product prototypes over the internet. Protocol analysis products are available from Gateway Communications at 800/367-6555, Triticom at 612/937-0772, and Intel at 800/538-3373. The LANalyzer In the NetWare environment, a product called LANalyzer for Windows is available to help managers monitor network operations and analyze packet traffic on Ethernet and Token Ring networks that use IPX, TCP/IP, and AppleTalk protocols. LANalyzer is discussed here as a typical protocol analyzer. It runs as software on a management station. You can go to Novell to find the latest information on LANalyzer. You use LANalyzer for daily or periodic monitoring of the network. Periodic monitoring can produce long-term trends that help you observe changes in network traffic. These trends might point out potential problems or identify users who are requesting excessive network services. With LANalyzer, you can correct or adjust the hardware and settings of a network before problems occur. You can also pinpoint the source of problems causing slow network response, failed connections, and excess network traffic. The LANalyzer window is shown in the figure below. It consists of the Dashboard and several fields that display current and long-term statistics about the network. 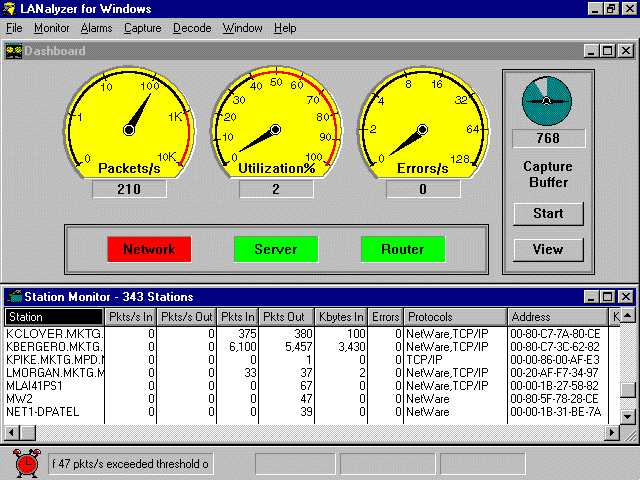
The figure below shows a typical packet capture window. In this case, a word-processed document file is transferred to the server. The summary window shows a list of packets transmitted. You can click on any packet to view detailed information about it, which appears in the middle decode window. At the bottom is a hexadecimal window that shows the contents of the packet. LANalyzer has a filtering feature that lets you specify a particular workstation for analysis, and/or the types of packets you want to view. You can also filter on a specific protocol, such as NetWare IPX, AppleTalk, or TCP/IP. 
LANalyzer also has graphing capabilities. A graph can show real-time events or display historical data for trend analysis, you can also print station monitor data, packet capture data, and graphs, or import the data into a spreadsheet for custom analysis. TFTP:Trivial File Transfer Protocol is a file transfer protocol with minimal requirements. It is specified in RFC 783 (Sollins, 1981) and uses UDP port 69. Like FTP, TFTP also supports a text and a binary transmission mode. The main difference for FTP is the use of a connectionless transport protocol, UDP in our case. This has several consequences as far as the structure of the protocol is concerned. First, the TFTP must itself be responsible for transmission reliability via algorithms such as time monitoring and packet re transmission. Moreover, the process does not involve logging on to the server computer; the TFTP server replaces this lack of authorization by restrictive access contraints, so that, for example, on UNIX processors, files may only be read and written to if their access rights make them available to be read and written by all users. The protocol specification does not prescribe how a system should protect itself against illegal access over TFTP, so this is therefore implementation specific. The TFTP protocol codes are:
Communication between the TFTP server and the client begins with RRQ or WRQ packets. In this way, transaction IDs are exchanged which are later used to identify the data packets. They also contain the file names and an entry regarding the transmission mode to be used. DATA packets are used to transmit the actual data and the server receives an ACK or an ERROR packet in reply. The transmission is deemed to be closed when DATA packet of length less than 512 bytes is received. It is not difficult to see that TFTP can have no advantages as far as regular file transfer between systems is concerned. While TFTP is used for such purposes in exceptional cases, the protocol is currently used in loading server programs and fonts in X window terminals and in bootstrapping diskless workstations. In the latter case, TFTP is used to transfer the system program into the main memory (see RFC 906 (Finlayson, 1984)). This is because of the low operational requirements of TFTP: in addition to the protocol itself, only the IP base functions, the very simple UDP protocol and a driver to access the network are required. Such a protocol may be implemented very cheaply and result stored in a few kilobytes of memory, for example, on a EPROM. tftp:As usual, UNIX systems contain a tftp command corresponding to the TFTP protocol of the same name. The corresponding server is called tftpd. The options available and the operation of tftp are very similar to the ftp command, but less comprehensive ( for example, the authorization process is missing). The user should note the access constraints referred to earlier. Below shows a sample tftp dialogue on a UNIX system. Here, the connect command does not establish a connection but determines the partner address for subsequent actions. verbose and trace make the exchange of the protocol elements visible.
$tftp Cabling scheme using 50-ohm coaxial cable with N-type connectors. Thicknet uses a 50-ohm coaxial cable as the backbone for the network. The cable has an outer diameter of 0.37 to 0.41 inches, depending on the type of insulation; also note that Thicknet cable has two layers of shielding. See also 10Base5. ThinNet:Cabling scheme using 50-ohm coaxial cable with BNC-type connectors -- thinnet coax is 0.20 inches in outer diameter and has a single layer of shielding. Sometimes called cheapernet. See also 10Base2. Threads:Threads are parts of processes that execute in multitasking operating systems. A multitasking operating system can run several programs or processes at once. Every process has a certain amount of work that needs to be done, and this work can be split into one or more parts or units that execute as threads. If the system has only one processor, then each thread is executed in turn, one after the other. A single thread does not dominate the processor, but instead is given a small amount of time to complete some or all of its tasks. Users have the illusion that several programs are running at the same time. Multiprocessor systems can help improve the performance of multitasking operating systems. Each thread can run on a separate processor at the same time. Processes run faster because multiple processors work together to complete tasks. Threads are useful because they eliminate the need for the operating system to constantly load and unload information to and from memory. The information required for each thread is kept in memory. This reduces overhead, not only in memory space, but in the time it takes to create the information in memory. Each thread may interact with a different part of the system, such as disk systems, network input/output (I/O), or the user. Threads are scheduled for execution because some may need to wait for events to occur or the completion of a task by another thread. Microsoft Windows NT and NetWare are multiprocessing and multithreaded operating systems. The thread scheduler for NetWare 4.x has been improved to enhance performance further. Microkernel operating systems such as Carnegie-Mellon University's Mach also take advantage of multiprocessing and multiprocessor systems by using threads. Mach, as the core for new UNIX systems, will provide multithreading capabilities. Throughput:The amount of work performed by a computer or related device or the amount of data passed through a network over a period of time. Basically it is the real speed that data is transmitted over a wire. Generally there is some overhead associated with sending data and ensuring that it arrived safely. This overhead can be as high as 25 percent of the bits on the wire. Time-domain Reflectometer:Sophisticated network troubleshooting equipment/tool that can pinpoint the location of electrical shorts and breaks, locate cable in walls, and measure the exact length of cable segments. Time Division Multiplexing (TDM):Time division multiplexers are digital devices and therefore select incoming bits digitally and place each bit into a high-speed bit stream in equal time intervals. The sending multiplexer will place a bit or byte from each of the incoming lines into a frame. The frames are placed on high-speed transmission lines, and a receiving multiplexer, knowing where each bit or byte is located, outputs the bits or bytes at appropriate speeds. Time division multiplexing is more efficient than frequency division multiplexing, but it requires a separate modem. To the sending and receiving stations it always appears as if a single line is connecting them. All lines for time division multiplexers originate in one location and end in one location. TDM's are easier to operate, less complex, and less expensive than FDM's. Token:An electronic message that is passed from station (computer) to station. The station with the token has the right to transmit on the network wire. This station must pass the token along to the next station after broadcasting for a maximum time. See also Token Ring, ARCNET, ARCNETPLUS, and Token Bus. Token Bus:A network topology in which all the stations can be placed on the same line, excluding hubs, and a token is used to give permission to send on the network. Examples are Token Ring, Token Bus, ARCNET, and ARCNETPLUS. Token Passing:A network access method in which devices on a network pass a special sequence of bits, known as the 'token', from one device to the next. A device can only transmit data on the network if it is in possession of the token. Another point of view is that token passing is different from both of the carrier-sensing methods. As the name suggests, token passing involves sending an electronic token packet on the network form one computer to the next; this token gives the receiving computer permission to transmit data. When that computer is finished sending its data, it then passes the token on the next computer. This is much like going around a table at a meeting and asking each person at the table if that person has anything to say. Token Ring:An industry standard (IEEE 802.5) network type that is commonly used to connect IBM mainframes and IBM PCs. Token Ring networks are arranged in a ring topology (architecture) in which devices pass tokens from one attaching device to another. Topology:The physical layout of a network, including the cables and devices. The topology of a network is its road map and can show which devices can communicate directly and which cannot because they don't share a connection path. Typical topologies used on local networks are the bus, star, and ring. Topology can also mean the possible logical connections along the network. Logical connections are those that permit nodes to communicate through some additional software processing instead of directly through physical connections. Transaction: (Database)An operation or series of operations applied against a database. Transceivers:The electronics hardware that physically connects to the ethernet backbone (main cable) or transmission medium. It is the connecting point for all devices on the ethernet cable that allows communication to pass back and forth over the backbone. For example the transmissions are sent and received from one computer to another computer somewhere else on the network. Ethernet transceivers contain analog electronics that apply signals to the cable and sense collisions. Another way to look at a transceiver is that it is a device used as an interface between a workstation and the network to which it is attached. The transceiver performs the task of transmitting frames onto the cable and receiving them from it. It also monitors signal levels on the medium and detects collisions and other error conditions, such as distinguishing between true network signals and noise. Transmission System:The essential function of a network is to transfer information between a source and a destination. The source and destination typically comprise of terminal equipment that attaches to the network, for example, a telephone or a computer. This process may involve the transfer of a single block of information or the transfer of a stream of information. The network must be able to provide connectivity in the sense of providing a means for information to flow among users. This basic capability is provided by transmission systems that transmit information by using various media such as wires, cables, radio, and optical fiber. Networks are typically designed to carry specific types of information, for example, analog voice signals, bits, or characters. Tree Topology:See Bus Topology. Trigger: (Database)A procedural function designed to execute when a table is modified. Trunk:A section of the network designed to handle heavy traffic, connecting many sub-networks. Also called a backbone. T-Span:To obtain access to lines that support speeds beyond those available in standard dial-up or leased telephone lines, a firm may actually buy a bundled set of digital lines. These digital private-line services are tariffed by the phone companies and referred to as T-span services. Tuple:A type of data in which two values or more (attributes) are combined with each other because the items are related; for example, in the routing table, the two items are a network number and the distance the network is away, measured in hops. Twisted-Pair Cable:Ordinary telephone wire consisting of two insulated copper strands twisted about each other to reduce outside interference of their signals. Twisted-pair wiring is relatively inexpensive, easy to install, easy to modify, and may already exist in may installations as part of the telephone network. See shielded cable and 10BaseT. The twists also provide protection from the crosstalk produced by nearby cables. The Twisted-pair cable is available in the following categories:
| |||||||
| Back | Home | Top | Feedback | Site Search |
 E-Mail Me |
This site is brought to you by This page was last updated on
09/18/2005 |
This Page has been accessed "9029" times.