| RDB PRIME! Engineering |
|
|
|
|
|
|
||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
|||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
| It is 16:00 PST on Monday 10/06/2025 | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
N, or Nano .. to .. Null Modem
N, or Nano: Used, usually in lowercase, as an abbreviation for the prefix nano, as in nsec (nanoseconds) or nm (nanometers). This order of magnitude corresponds to 2-30 which is roughly 10-9, or one billionth (in the United States counting system). Also see Order of Magnitude. Name-Binding Protocol (NBP):The Name Binding Protocol (NBP) is important in the AppleTalk scheme of things. To maintain communications, the network itself operates with numeric internet addresses, but the AppleTalk user works with named entities. AppleTalk internally represents any named entity, which is a network service such as a file server or a network device such as a Mac, according to the following conventions: object:type@zone In this line, object is the name of the user or service name, type is the entity classification, and zone is the logical zone of the AppleTalk internet. Given these conventions, then, consider the following line: Bldg. 3 Printer:LaserWriter@TekServers In this line, Bldg. 3 Printer represents the object; LaserWriter represents the type; and TekServers represents the zone. These conventions are only used internally by AppleTalk protocols; the Chooser serves as the user's interface to named entities (see the figure below). 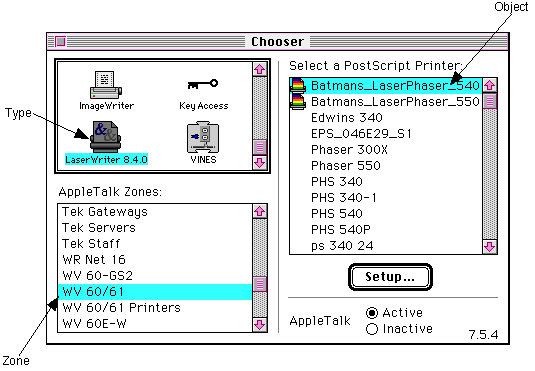 The Chooser is the user's interface to selecting named entities on AppleTalk. When you select one of the icons shown in the Chooser, you're selecting the device type; the zone list is shown below the list of icons, and the list of objects matching the selected type is displayed in the right half of the Chooser dialog box. The Name Binding Protocol handles the translations between the numeric internet addresses and alphanumeric entity names. The NBP Protocol maintains a table of mappings (a names table) between internet addresses (a node) and name socket clients (named entities) that reside in that node. Because each node maintains its own list of named entities, the names directory within an AppleTalk network is not centralized, but is a distributed database of all nodes on the internet. This approach to storing entity names requires that a socket that needs to communicate with a named service must first find out where the service is by requesting its location. This request is made via the NBP Broadcast Request (BrRq) packet, which names the desired entity and requests the network address for that named entity. On a single network, each node responds to the NBP Broadcast Request (BrRq) and searches its internal names table for a match. When a match is found , NBP sends a LookUp-Reply to the requesting socket, including the address of the named entity, see figure below. 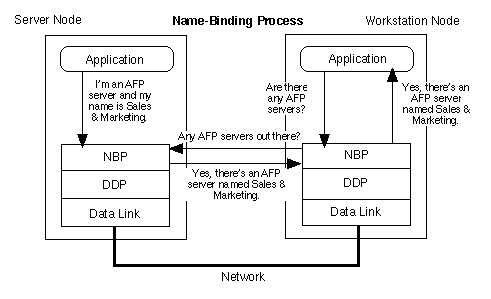 If the request is made on an internet, the router forwards the BrRq to each network in the specified target zone, causing the affected nodes to perform the search of their names tables. In the example given above, the workstation sends an NBP LkUp for AFP servers. The server node named Sales & Marketing then replies that it is an AFP server and supplies its network address. Including the name lookup feature just described, NBP provides a total of four services to accomplish this search:
Name registration, which takes place on each node, is used to build the names table. Name deletion, the opposite of registration, occurs when an entity has its name and socket number removed from the names table. The final is name confirmation, which can be used to validate a name-address binding, to see whether it has changed since the last lookup. Named Pipes:In many operating environments, a stream that can be used for the exchange of information between two processes (programs). The pipe can be referred to by name, and the storage allocated for the pipe can be accessed and used for reading and writing, much like a file, except that the storage and the pipe disappear when the programs involved finish executing. Named pipes is a high-level interface for passing data between processes that are running on separate computers connected by a network. Named pipes is an extension of the OS/2 operating system that is implemented on Microsoft LAN Manager and IBM LAN Server network operating systems. It is the network version of interprocess communication (IPC) facilities, which provide an interface between processes running in a single, multitasking system. Named pipes is part of a group of interprocess communication facilities in the OS/2 environment (and some other environments) that are used by concurrently running processes that need to communicate with one another. These include:
Compared to a pipe, a named pipe is a "communication process" between two remote computer systems that are attached to a network. A logical connection is set up between the two remote processes (programs) and the transfer of information takes place over the physical network. The most important aspect of named pipes is that they enable client-server applications in distributed computing environments. A process on a front-end client machine (host) can interact with a process on a back-end server machine. For example, a client can make requests for files on a network file server or query a database on a remote database server. The named pipes interface is better at handling network transactions than NetBIOS and can do so with a single call compared to the many operations required to perform the same actions through NetBIOS. However, the named pipes interface does not provide features of NetBIOS such as connectionless datagram services and the naming functions that allow messages to be sent to groups. Related groups of information are associated with: Interprocess Communication, Mail Slots, Messaging API, Inter-Application, NetBIOS/NetBEUI, Pipes, Remote Procedure Call, and Server Message Block. Named Resolution:In a network or internetwork, name resolution refers to the process of mapping a name of a device or node to an address. Named Space:A name space is a NetWare Loadable Module (NLM) that makes it possible to store non-DOS files on a Novell NetWare file server. You can store Macintosh, UNIX, OS/2, or other types of files on a NetWare 3.x or later server by linking the appropriate name space NLM to the operating system. You also must use the ADD NAME SPACE utility to add configuration information for the name space. The volume to which the alien file is being added will create two directory entries for the file: a DOS entry and an entry with the information for the file's native format. Adding a name space to a volume has its costs:
See also NetWare. Namespace:(1) The set of names in a naming system. (2) A logical grouping of the names used within a program. Also called name scope. (3) A library of classes in .NET. (4) XML namespace: In XML, a namespace is a collection of names, identified by a URI reference, that are used in XML documents as element types and attribute names. In order for XML documents to be able to use elements and attributes that have the same name but come from different sources, there must be a way to differentiate between the markup elements that come from the different sources. (5) DNS namespace: DNS is the name service provided by the Internet for TCP/IP networks. DNS is broken up into domains, a logical organization of computers that exist in a larger network. The domains exist at different levels and connect in a hierarchy that resembles the root structure of a tree. Each domain extends from the node above it, beginning at the top with the root-level domain. Under the root-level domain are the top-level domains, under those are the second-level domains, and on down into subdomains. DNS namespace identifies the structure of the domains that combine to form a complete domain name. For example, in the domain name sub.secondary.com, "com" is the top-level domain, "secondary" identifies the secondary domain name (commonly a site hosted by an organization and/or business), and "sub" identifies a subdomain within the larger network. This entire DNS domain structure is called the DNS namespace. The name assigned to a domain or computer relates to its position in the namespace. Naming Service:A naming service is a mechanism that makes it possible to name resources on the network and to access them through those names. This service associates a more easily remembered name with a network entity, and that name can then be used instead of the resource's network address. Naming services are available in most network operating systems. A naming service can be either of two types:
For example, Novell's NetWare versions prior to 4.0 use a local naming service; information about the resources associated with a server is stored in a resource database known as the bindery. The NetWare Directory Services (NDS) used in NetWare 4.x is an example of a global naming service. Another example is StreetTalk, the global naming service for Banyan's VINES. With a global naming service, each object on the internetwork has a unique name, so you do not need to know the name of a server to find an object associated with that server. Also see Bindery, NetWare Directory Services (NDS), and/or StreetTalk. Nano:A billionth (10-9). A nanosecond is one-billionth of a second. NAS: (Harddrive)Network Attached Storage, a storage design that connects a server to externally enclosed hard drives via a local area network. National Computer Center (NCC):The National Computer Center (NCC) in Britain is one of the centers that has developed automated software for testing compliance with X.400 and X.500 standards. These centers develop test engines based on the abstract test suites specified by the ITU (International Telecommunication Union). Other centers include the NVLAP (National Voluntary Laboratory Accreditation Program) in the United States, Alcatel in France, and Danet GmbH in Germany. NCSA:National Center for Supercomputing Applications at the University of Illinois, Urbana-Champaign. Headquarters of the National Computational Science Alliance, part of NSF's PACI. Need: (UML)A reflection of the business, personal, or operational problem (or opportunity) that must be addressed to justify consideration, purchase, or use of a new system. NetBEUI:NetBEUI was developed by IBM in 1985 as a network transport protocol for small- to medium- sized LANs. NetBEUI is supported by Microsoft in its networking products, including Windows for Workgroups and Windows NT. IBM and Microsoft networks can communicate due NetBEUI and NetBIOS implametation. NetBEUI is a Transport and Network layer protocol in relation to the OSI protocol model. It integrates with NetBIOS to provide an efficient communication system in the workgroup LAN environment. NetBEUI provides the data transport services required by NetBIOS. Think of a phone call. NetBIOS is like the person making the call and NetBEUI is like the control program that works with the underlying switching system to complete the call. NetBIOS:NetBIOS was designed with the premise that PCs on a LAN only need to talk to other PCs on the same LAN. It is a Session layer protocol in relation to the OSI protocol model and was originally developed by Sytek Inc., for IBM to use in its broadband networks. It was devloped in 1984. NetBIOS is an application program interface (API) that programmers use to create LAN applications for the IBM LAN server, Microsoft LAN Manager, and OS/2 environments. Named pipes are a network extension of OS/2 that provides similar but more advanced features. NetBIOS and named pipes exist in the LAN environment as the protocols on which various applications are built. NetBIOS provides the following services:
Servers use the broadcasting feature of NetBIOS to locate the workstations and devices in its domain (management zone). If a workstation responds to the messages, the server no longer sends it messages. If a workstation doesn't respond because it is turned off or has a defective network interface card (NIC), the server sends messages every few minutes in an attempt to get a response. Because the messages are sent everywhere on the network, including WAN links, they get expensive in terms of bandwidth usage and WAN link costs. A Remote Name Directory (RND) function can be used to turn these broadcasts into nonbroadcast datagrams that don't cross WAN links. NetBIOS is well established and still supported in many environments, even though newer protocols such as named pipes are available. NetBIOS is also well understood and there are many applications that use it. It will be around for some time. See related entries such as Named Pipes; Routing Protocols; Windows for Workgroups, and Windows NT. NETBIOS.EXE:A NetBIOS emulator program used in Novell's NetWare network operating system. This emulator makes it possible to run applications that use NetBIOS-based peer-to-peer or distributed communications (as opposed to using a server-based communications model, as NetWare). NetPartner:A network management system from AT&T. NetPartner can monitor voice and data links for wide-area networks. NetView (IBM):NetView is a mainframe network management product from IBM. It is used for monitoring SNA (Systems Network Architecture)- compliant networks. NetView runs as a VTAM (Virtual Telecommunications Access Method) application on the main-frame that is serving as network manager. NetView Components NetView includes the following components:
NetView uses the Network Management Vector Transport (NMVT) protocol to communicate with management agents operating at entry points (which connect SNA-compliant devices to NetView) and service points (which connect non-IBM devices or networks). Many of NetView’s features have been incorporated into IBM’s LAN Network Manager, which is used to manage Token Ring networks. LAN Network Manager can work together with NetView, such as when the LAN is part of a larger, SNA network. Novell’s NetWare Management Agent for NetView also provides NetView support for NetWare servers running a Token Ring network. This product consists of several NetWare Loadable Modules (NLMs) that can forward NetView alerts to a NetView host machine and can also respond to requests from a NetView host for maintenance statistics. NetView/PC: A related product, NetView/PC, provides an API (Application Program Interface) that enables developers to interface NetView with new hardware or software. NetView/PC can be used as a manager for its own network. As such, the program can gather performance, usage, and billing information. NetView/PC also makes it possible for non-IBM devices, LANs, or even certain types of PBXs (private branch exchanges) to connect to an IBM NMA (Network Management Architecture) network. Other areas of interest -- Network Management; NMA (Network Management Architecture)NetView/PC NetWare:NetWare is a network operating system (NOS) from Novell. Several different versions of NetWare are currently (or have been) available. These versions differ in the hardware they support, in the networking services they provide, and in special features (such as fault tolerance). Early NetWare Versions:
The earliest versions of NetWare -- Newer NetWare Versions: Valuable features from earlier versions (for example, fault tolerant capabilities such as disk mirroring) were incorporated into NetWare v2.2, which was released in 1991. The table "NetWare Versions and Features" lists the newer NetWare versions and summarizes some of their features. Note that later versions of NetWare generally inherit the features of earlier versions (a NetWare 3.x server can do anything a NetWare 2.x server can, a NetWare 4.x server can do whatever a NetWare 3.x server can and so on). Also note that the NetWare versions have many more specific features along with the ones included in the table's summary.
NetWare Components: Server-based versions of NetWare (NetWare 2.x, 3.x, and 4.x) consist of two components:
Server Software: The NetWare program running on the server is an NOS (Network Operating System). NetWare has its own partition on the hard disk, and it may replace the native operating system (for example, DOS) as the program with which applications and other precesses deal. In other cases, NetWare may run as a process under the operating system, as does NetWare for UNIX. Even when it becomes the primary operating system, NetWare may still rely on the native operating system. For example, NetWare for DOS uses some DOS services as well as the DOS file system. The capabilities of the NOS running on a server depend on several things, including the following:
Workstation Software: The software on the workstation in a NetWare network must be able to communicate with the network and also with the workstation's operating system. The workstation software determines whether a request from a program or user is intended for the workstation (that is, for DOS) or for the network. If the request is for the workstation, the software passes it on to DOS. If it is a network request, the software does the following:
Once the packet is passed to the NIC, the workstation component of the NOS is finished with its task. The software running the NIC does further processing and makes sure the packet gets onto the network. For DOS workstations, the program that does these things is called the NetWare shell is versions preceding 4.x. In NetWare 4.x, this software is known as the NetWare DOS Requester. The DOS Requester software runs as a DOS process, but takes considerable control by intercepting certain key DOS interrupts. This is done so that network related requests go on to the network. The workstation software consists of several utilities, each responsible for one of the shell's tasks. These utilities include NETx.COM, SPX.COM, and IPX.COM. NETx dos the intercepting, redirecting, and the first round of processing (into Network Control Program (also Point) (NCP) form); Sequenced Packet Exchange (SPX) and Internetwork Packet Exchange (IPX) create packets designed for their counterpart programs at the destination. The DOS Requester (NetWare 4.x) consists of a collection of Virtual Loadable Modules (VLMs), which are modules running on a workstation. The VLMs accomplish generally the same kinds of tasks as the shell utilities, but do so in different ways. NetWare Directory Database (NDD):In the NetWare Directory Services (NDS) for Novell NetWare 4.x, the NetWare Directory Database contains the object information. This information is represented in a hierarchically organized tree structure. This database is commonly known simply as the Directory (with capital D). NetWare Express:A private electronic information service from Novell. Subscribers can access the Novell Support Encyclopedia and the NetWare Buyer's Guide, and they can get product information and technical support. To access this service, delivered over the GE Information Services Network, users need the appropriate software and an asynchronous modem. There is a fee for this service. NetWare for Macintosh:Is a collection of NetWare Loadable Modules (NLMs) that provide various NetWare services, including file handling, printing, network administration, and AppleTalk routing, for Macintosh clients on a Novell NetWare network. With NetWare for Macintosh, Macintosh users can access network resources, files, and applications, send print jobs to network printers, and take advantage of NetWare features, such as network security. Users also get access to the NetWare Directory Services (with version 4.x of the product), as well as access to AppleTalk print services. Thus, by running NetWare for Macintosh, users can get the benefits and resources accessible through a NetWare network, while keeping their familiar Macintosh interface. NetWare for UNIX:A program that provides NetWare support on machines running general-purpose operating systems, such as UNIX. NetWare for UNIX (formerly Portable NetWare) runs as a set of applications on the host. The software enables the host to provide file handling, printing, and backup services to clients, regardless of whether clients are running DOS, Microsoft Windows, or the Macintosh operating system. NetWare for UNIX is sold by the host system vendors. NetWare/IP:NetWare Loadable Modules (NLMs) that provide support for the IP (Internet Protocol) as a routing protocol for NetWare 3.x and 4.x servers. With NetWare/IP, a NetWare server can function as a gateway between NetWare and TCP/IP networks. NetWare Shell:In NetWare versions prior to 4.0, a terminate-end-stay-resident (TSR) program loaded on a workstation. The shell sits between the application environment and DOS. NetWare TCP/IP:A collection of NetWare Loadable Modules (NLMs) that implement the TCP/IP protocol suite in order to provide routing services for stations using the TCP/IP format. NetWire:An online information service run by Novell. NetWire provides product and technical information, and an opportunity to submit technical questions to Novell Technicians. NetWire is available through CompuServe. Network:A network consists of computers, call nodes or stations. The computers are connected to, or can communicate with, each other in some way. Nodes run special software for initiating and managing network interactions. With the help of networking software, nodes can share files and resources. Network Components: The following are the main hardware components of a network:
The software components include the following:
The component groupings, particularly for the software, are not mutually exclusive. The same software may be viewed as belonging in multiple categories. For example, a NOS (Network Operating System) can include various network resources and tools. Because of the connection and the software, nodes on the network can communicate and interact with each other. The interaction may be directly between two nodes, via one or more intermediate nodes, or through a server node. The interaction can be over a physical medium (such as electrical or fiber-optic cable) or by wireless means (using radio waves, microwaves, or infrared waves). Users working on a network node can make use of available files and resources on other nodes as well. Each user generally has a limited range of access and usage privileges, which are monitored and controlled by the NOS. A (human) network administrator, or manager, oversees the NOS's configuration and operations. The administrator sets the user privileges. Network Categories: Networks come in all shapes and sizes, and can be categorized using a variety of features and functions. These categorizations are neither exclusive nor exhaustive, but they do yield a rich crop of terminology, as summarized in the table "Network Groupings" below. The various groupings are described in the following sections. Keep in mind that networking categories and terminology may overlap, complement, or be independent. For example, one person's local-area network (LAN) may be another's campus-area network (CAN). Networks Classified by Capacity: A network may be able to transmit one or more messages at a time. A baseband network can transmit exactly one message at a time. Most LANs are baseband networks. A carrierband network is a special case of a baseband network. In this type of network, the channel's entire bandwidth is used for a single transmission, and the signal is modulated before being transmitted. A broadband network can transmit more than one message at a time by using a different frequency range for each message and then multiplexing these multiple channels (sending all the messages out on a single channel). NETWORK GROUPINGS
Networks Classified by Transmission Rate: In general, broadband networks support higher transmission rates. However, there is considerable variation in transmission rates for baseband networks, and there is considerable overlap in transmission rates. That is, there are lots of baseband networks that are faster than some broadband networks, even though broadband networks tend to support higher rates. Very roughly, we can distinguish four generations of networks:
Networks Classified by Range: Networks are distinguished by the range over which the nodes are distributed. Interestingly, the number of nodes is not used as a major distinction (except by network software vendors when they sell packages to end-users). The table "Network Range Categories" below summarizes the types of networks in this classification. See the article about the specific network type for a more detailed discussion. The most common categories are LANs, WANs (wide-area networks), and MANs (metropolitan-area networks), but GANs (global-area networks) will become increasingly popular as multinational corporations connect all their operations. LANs generally include only PCs. WANs generally include some type of remote connection. Enterprise networks typically require gateways to access the mainframe-based networks. Networks Classified by Types of Nodes: PC-based networks are the fastest growing segment of the networking world. Such networks offer the greatest flexibility in where to put servers and how to divide the services among nodes on the network. References to "LANs" generally assume a PC-based network. Most PC-based networks use either Macintoshes or IBM PC and compatible machines. Macintoshes come with networking capabilities built in; PCs require extra hardware (an Network Interface Card) to join a network. The whole gamut of PCs may be used in networks. For example, an IBM-based network may have machines ranging from an XT to a machine with an 80486 or a Pentium processor. Of course, key functions may be restricted to certain classes of machines. For example, some networking software allows only 80386 or 80486 machines as file servers; older machines can be used only as workstations or "smaller" servers (such as print or tape servers). NETWORK RANGE CATEGORIES
Use of superservers, which are souped-up PCs specially designed to be used as file servers, is becoming more popular. This is because hardware capabilities have reached a level at which it is feasible for a single machine to serve dozens of nodes, and possibly to serve nodes with different network architectures at the same time. To manage multiple architectures, a superserver needs the appropriate hardware for each architecture. (See the articles about servers, NICs (Network Interface Cards), and the individual network architectures for more information). Networks that include minicomputers or mainframes are usually located in either business or university environments. In the business world, such networks are generally run by an MIS department. Historically, these network environments have been dominated for several decades by IBM main-frames. Minicomputers, produced by companies such as Digital Equipment Corporation (DEC) or Wang (and even IBM), made inroads only slowly in the business world. In the early days, minicomputers were used as front-end processors (FEPs) for mainframes. Mainframe-based networks generally consist mainly of terminals, which communicate directly with the mainframe or through FEPs. PCs can be used in the place of terminals, but the PCs must run terminal-emulation software and may need to "play dumb" (pretend to be nothing more than a terminal) to communicate with the mainframe. Mainframe-based networks generally use software that complies with IBM's SNA (Systems Network Architecture) and, if PCs are to be included as more than dumb terminals, SAA (Systems Applications Architecture). SNA and SAA provide comprehensive models (comparable to the seven-layer OSI Reference Model) for controlling the details of network operation and communication at several levels. DEC's alternative to SNA is DNA (Digital Network Architecture), which provides a framework for networks built around mini-computers (such as DEC's VAX machines). DECnet is one example of networking software based on the DNA framework. In university settings, distributed networks are quite common. In such networks, there is no centralized controller. Instead, nodes are more or less comparable, except that certain nodes provide the services available on the network. UNIX environments are particularly likely to use a distributed network architecture. Minicomputer- and mainframe- based networks often provide services to LANs. Nodes on the LAN get access to the mainframe- based network through gateways. The real advantages of layered architectures become particularly clear in such interactions between the very different worlds of the LAN and an SNA-based network. Backbone networks are designed with smaller, access networks as nodes. Such networks are able to provide the advantages of very large, heterogeneous networks while also allowing the simplicity of a LAN. The access networks can operate as independent networks for the most part, but can get access to resources in any of the other networks linked to the backbone, provided, of course, that the access network has the appropriate usage privileges. Networks Classified by Relationships among Nodes: Nodes on a network can be servers or workstations. A workstation makes requests, and a server fulfills them. The "server" actually controls the network by providing the user at the workstation with only the resources the server sees fit. With the introduction of products such as NetWare Lite, Personal NetWare, LANTastic, and Microsoft Windows for Workgroups, peer-to-peer networks have been gaining in popularity. The following terms are used to describe the relationship between nodes in a network:
In the most general form of client/server computing, the workstation makes a query or request, and the server processes the query or request and returns the results to the workstation. In a commonly used form, a front-end process running on the client sends a query or request to the back end running on the server. The back end does the requested work and returns the results to the client. Networks Classified by Topology: There are thousands of ways you can connect computers into a network. Fortunately, these possibilities all reduce to a few fundamental types (just as all the possible wall-paper patterns reduce to about two dozen basic patterns). When discussing network layouts, or topologies, it is useful to distinguish between the physical and logical layouts. The logical topology specifies the flow of information and communication in the network. The physical topology specifies the wiring that links the nodes in the network. Logical Topologies: The two main logical topologies are bus and ring. In a bus topology, information is broadcast along a single cable, called the trunk cable. All nodes attached to the network can hear the information, and at roughly the same time. Only nodes for whom the information is intended actually read and process the transmitted packets. The information broadcast and simultaneous access characterize a bus topology. Because all nodes hear a transmission at the same time, contentious network-access methods, such as CSMA/CD (Carrier Sense Multiple Access/Collision Avoidance), can be used. In contentious media-access methods, nodes get transmission rights by being the first to request them when there is no network activity. The figure "A linear bus topology" illustrates this logical topology.
A LINEAR BUS TOPOLOGY In a ring topology, information is passed from node to node in a ring. Each node gets information from exactly one node and transmits it to exactly one node. Nodes gain access to the message sequentially (in a predetermined sequence), generally based on network addresses. As with all networks, a node is expected to process only those packets with the node as a destination. Because all nodes do not hear a transmission at the same time, network-access methods cannot be based on contention for transmission rights. Instead, deterministic-access methods, such as token passing, are used. The figure "A ring topology" illustrates this logical topology.
A RING TOPOLOGY Physical Topologies: Whereas the logical topology controls how information moves across a network, the physical topology, or wiring scheme, controls how electrical signals move across the network. This has consequences for the status of a network if a node breaks down. For example, a bus wiring scheme requires minimal cable, but can make troubleshooting more difficult than with, for example, a star wiring scheme. If a node attached to the bus over a drop cable goes down, there may be no way for the server to know this until the server tries to send the node a message and gets no response. In contrast, a star wiring scheme uses lots of cable, since each node may be a considerable distance from the central node or hub, but it is easy to determine when a node goes down because the central node can communicate directly with each node. Although there are dozens of ways to label network wiring schemes, most of these fall into the following major groups:
BUS NETWORKS The figures "A star topology" and "A star-wired ring topology" illustrate these two types of physical topologies.
A STAR TOPOLOGY
A STAR-WIRED RING TOPOLOGY These four schemes capture most of the network wiring configurations, but there are other ways of categorizing the network layout. For example, in a mesh topology, a node may be connected to one or more other nodes. In the extreme case, every node is connected directly to every other node. The advantage of direct access to each node is more than offset by the wires that will be running everywhere and by the fact that each node will need a port for connecting to every other node. Networks Classified by Architecture: Network architectures differ in the cabling used (coaxial, twisted-pair, fiber-optic), the methods used to access the network (CSMA/ CD, token passing, polling), the format of data packets sent across the network, and the network topology. In general, different network architectures need translators in order to talk to each other. Routers and multiarchitecture hubs help to make such cross-architecture communications transparent to users. The most commonly used network architectures are Ethernet/IEEE 802.3, ARCnet, Token Ring, and FDDI. See the Network Architecture article for more information. Networks Classified by Access Possibilities: Networks can be shared-media or switched. In standard, shared-media network architectures (such as Ethernet or Token Ring), only one node can transmit at a time. That is, access to the network medium is exclusive. How a node gets access to the medium depends on the access method used (for example, CSMA/CD versus token passing versus polling). Switched networks, in contrast, establish temporary connections as needed between parties. Such networks use multiplexing to enable multiple nodes to transmit at the same time. The basis used for the switching distinguishes such networks. Networks can be packet-switched, circuit-switched, or message-switched. ALTERNATIVES TO NETWORKS The following alternatives to networks have been used and should be considered before you go to the trouble and expense of creating your own network, especially if your main needs are for file sharing:
Planning a Network: If you are planning to set up a network, you should seriously consider hiring a professional consultant to help you. Be sure to make the prospective consultant prove to you that he or she is competent. Also consider the article on Network Lifecycle. Before investing in a network, planning is essential. Always make sure you have all available information to guide your planning. The following are some guidelines to follow when you begin planning for a network:
CALCULATING AVAILABLE RESOURCES To play it safe, after you've determined the available resources, use only a portion of these for your working calculations. This downgrading will protect you against the inevitable resource losses and sags due to people leaving, becoming involved in other projects, and so forth. The amount by which you need to decrease your estimates depends on the possible costs if your network is a failure and also on how stable the resources are. As a general rule of thumb, assume your available resources will be anywhere from 10 to 50 percent less than you estimated. The converse of this coin concerns cost calculations. When you decide how much time and money things will cost, it's a good idea to add an amount or a percentage -- as a hedge against Murphy's laws. Chances are only moderate (at best) that you will be able to use the wiring—except, possibly, for short-hauls and special-purpose connections. On the other hand, if you can do it, this can save a considerable amount of money, since cable installation is a major chunk of network cabling expenses. Once you've decided that a network is the appropriate solution for your needs, a second phase of planning begins. In this phase, the components and details of the network are designed. Later phases include implementing and actually running the network. See the LAN article for a more detailed discussion of LAN planning. SEE ALSO -- Network, Circuit-Switched; Network, Message-Switched; Network, and Packet-Switched. Network Access Controller (NAC):An Network Access Controller (NAC) is a device that provides access to a network, for remote callers or for another network. Network Addressable Unit (NAU):In IBM's SNA networks, an NAU is any location with one or more ports for communication over the network. The three types of NAUs are PUs (Physical Units), LUs (Logical Units), and SSCPs (System service control points). Also look at SNA (Systems Network Architecture). Network Administration:Network administration refers to the task of managing and maintaining a network, to make sure all programs are up to date, all hardware is functioning properly, and all authorized users are able to access and work on the network. A network administrator, or manager, must do tasks such as the following:
SEE ALSO LAN (Local-Area Network) Network Analyzer:A network analyzer is a product that can be used to monitor the activity of a network and the stations on it, and to provide daily summaries or long-term trends of network usage and performance. A network analyzer can do tasks such as the following:
Network analyzers may be software only or may consist of both software and hardware. The latter may include an interface card for testing the network directly. This card may even include an on-board processor. Because of their greater capabilities, hardware/software analyzers are considerably more expensive than software-only products. Prices for the hardware/software packages can be several times as high as for software-only products. Network Architecture:Depending on the scope of the discussion, a network architecture may refer to a model that encompasses an entire computing environment or to one that specifies just low-level features (cabling, packet structure, and media access) of a network. Examples of global (encompassing) architectures include IBM's SNA (Systems Network Architecture), DEC's DNA (Net-work Architecture), and the ISO's OSI Reference Model. Such architectures are used for wide-area networks (WANs) as well as local-area networks (LANs). Network Byte Order:For any two computers to be able to communicate, they must use a common data format while transferring the multibyte words. The Internet adopts the big endian format. This representation is known as network byte order in contrast to the representation adopted by the host, which is called host byte order. Network Information and Control Exchange (NICE):A proprietary application layer protocol from Digital Equipment Corporation (DEC). The protocol is used in DECnet networks for tesing the network and for getting information about node configurations. Network Interface Card (NIC):The NIC is the network component with a thousand names, including LAN adapter, LAN card, NIU (network interface unit), network adapter, and network board. An Network Interface Card enables a PC to connect to and access a network. The NIC communicates through drivers with the node's networking software (shell or operating system) at one end, and with the network (the cabling to the other nodes) at the other end. Network Interface Layer:The network interface layer is concerned with the the network specific aspects of the transfer of packets. . Network Layer:This is layer 3 in the OSI (Open Systems Interconnect) model. The network layer forms a logical connection between source and destination nodes on a network. It accepts messages from the higher layers, breaks them into packets, routes them to the distant end through the link and physical layers, and reassembles them in the same form in which the sending end delivered them to the network. The network layer controls the flow of packets, controls congestion in the netowrk, and routes between nodes to the destination. The X.25 protocol is a connection oriented layer 3 protocol for access to a packet-switched data network. Internet Protocol (IP) is one of the most widely used protocols in the world which, together with transport control protocol, forms a common language used in most internets. IP is a connectionless layer 3 protocol. Since TCP/IP predated the OSI model, its layer functions do not correspond directly to OSI. Network Interface Cards usually fit into expansion slots in a PC or Macintosh. *Network Lifecycle:The life cycle of a network is an important planning consideration because of inevitable technological changes that will have to be dealt with. Each network is a representation of the technology at the time of its design and implementation. Eventually, the network will become obsolete. New technologies and services will emerge, making it cost effective to replace outdated equipment and software with newer, more powerful, and less expensive technology. During its life cycle, a network passes through the phases outlined below:
This involves the subphases of problem definition and investigation. The problem definition attempts to find the problems that exist in the organization that caused management to initiate the study. The investigation subphase involves gathering input data to develop a precise definition of the present data communication conditions and to uncover possible problems. The analysis phase uses the data gathered in the feasibility study to identify the requirements that the network must meet in order to have a successful implementation. During the design phase, components of the network are defined, that is, Media type, NOS (Network Operating Systems or Systems, Gateways, Routers, etc. The implementation phase consists of the installation of the hardware and software that make up the network system. Also, during this phase all documentation and training materials are developed. During the maintenance and the upgrade phase the network is kept operational and fine-tuned by network operations personnel. Additionally, updates of software and hardware are performed to keep the network operating efficiently and effectively. Network File System -- A protocol developed by SUN Microsystems that uses IP to allow a set of cooperating computers to access each other's file systems as if they were local. The key advantage of NFS over conventional file transfer protocols is that NFS hides the differences between local and remote files by placing them in the same name space. Basically NFS allows files on remote nodes of a network to appear as if they were stored on the local workstation. NFS was designed for UNIX systems, but has been implemented on may other systems, including personal computers like the IBM PC and the Apple Macintosh. Network Fundamentals (OSI Layers):In order to simplify data movement among various end systems, it is pragmatic to modularize the communication mechanisms, so that each module behaves as a predefined communication standard. The OSIRM (Open System Interconnection Reference Model) is the standard for identifying the layers and the services provided in a communication system. There are seven layers of hierarchical communication system. Each layer provides a service to the layer above it. For example, the network layer provides a service to the transport layer, and the transport layer presents "data" to the internetwork system. The network layer encapsulates the data, passed down from the transport layer, within a network header. The header contains information such as source and destination logical addresses. The data link layer adds frame header and trailer to the encapsulated packet passed down from the network layer. The frame header contains the physical addresses. The physical layer provides the physical transmission medium (such as DS1, DS3, SONET (Synchronous Optical Network)) connections. Multiplexers, repeaters, and hubs are typical internetworking devices at the physical layer. Repeaters and hubs are physical layer relays in the OSI (Open System Interconnection) terminology; bridges are data link layer relays; and routers are network layer relays. Network Topologies:The configurations used to describe networks are sometimes called network architecture or network topology. Networks can have many different logical and physical configurations. However, regardless of how they are implemented, networks can be placed into one of the general categories below. The most common network topologies are:
Regardless of the configuration used, all networks are made up the same four basic components:
Networks can be further categorized into narrowband networks and wideband networks.
NeXTSTEP is an object-oriented variant of the UNIX operating system. It is based most immediately on the Mach variant developed at Carnegie-Mellon University. Like Mach and Windows NT, NeXTSTEP uses a microkernel architecture in which only a barebones operating system core (the microkernel) stays loaded; other services are provided in modules that can be loaded as needed. NeXTSTEP machines come with built-in support for thin and twisted-pair Ethernet. As a UNIX variant, NeXTSTEP supports the TCP/IP protocol suite, and NeXTSTEP machines can be either servers or clients on a TCP/IP network, very similar to Macintosh systems. They can also be Macintosh or NetWare clients; NeXTSTEP includes software that allows a NeXT machine to access file and print services on NetWare or AppleTalk networks. Optional add ons provide support for ISDN (Integrated Services Digital Network) and terminal-emulation capabilities for communications with IBM mainframes. NeXTSTEP can support file servers and services, using the Network File System (NFS) popular in certain UNIX networks. The operating system also supports NetInfo databases and provides servers for these databases. In addition, NeXTSTEP can provide mail, printing, and fax modem services. NeXTSTEP was designed originally as the native operating system for NeXT's hardware line. However, following the disappointing sales of NeXT machines, NeXT dropped out of the hardware business and has ported NeXTSTEP to Intel processors. Recently Apple Computer purchased the NeXT Software Company along with NeXTSTEP. The rumor is that Apple is going to use the NeXTSTEP micro kernel to update Apples existing OS to a true Multitasking, preemptive operating system. Nib Files:Nib files store the user interface of your application, including windows, dialogs, and user-interface elements such as buttons, sliders, text objects, and help tags for these elements. A nib file also holds the connections between these objects that cause actions to be performed when the user activates controls. Interface Builder (One of Apples XCode Tools) stores user interface resources in "nib" files. Nib files are "a statically stored representation of the set of interface objects used by the application and their relationships which can be efficiently brought into memory when needed, reducing development time and making it easier to localize an application for different markets," as Apple puts it. In other words, you can create .nib files, which "point" to resources in the OS, and are thus much smaller than they might otherwise be. They are also portable and reusable; check out the Nib Tool. Interface Builder is a great way to create Aqua-compliant GUIs on Mac OS X since it has facilities to help developers adhere to the guidelines. All the interfaces are stored in "nib" files which contain freeze dried objects, and not actual code. IB can be used to create interfaces for both Carbon and Cocoa applications, but the nib files are not interchangeable between the two APIs. A nib with Cocoa objects can only be used by a Cocoa app or a WO (Web Objects) Java Client app. When using nibs with WO Java Client, an actual code file is spit out with the nib. Carbon nibs can be used for Carbon apps on Mac OS X and Mac OS 9. Both Cocoa and Carbon interfaces can be tried out in IB's test mode. One of the most important performance tips, long known by expert Cocoa programmers, is to not put the whole UI (User Interface) into one big nib file. Doing this makes the application launch more slowly. Instead, you should break up your interface into several nibs. (A common rule of thumb is to never put more than one window in a nib file.) These other nib files should then be loaded only when they are needed by the application. For example, the user never invokes the find panel, then you never have to create objects for it which translates to a speed advantage and less memory usage. In addition to the speed benefits, by doing this you will also be able to reuse the object graphs archived in your nib files. Interface Builder now allows new "top level" objects inside a nib. A top level object is one which appears in the nib's Instances pane. In the past, this could be main menus, windows, and controllers such as custom NSObject instances. Now formatters can be there (facilitating reuse of a formatter between multiple UI elements) as well as windowless view objects and single level menus (for context menu creation). In a nib file, all top level objects have a retain count of one and it is the responsibility of the File's Owner to actually release all of these objects. If the File's owner doesn't release them all, then there will be leaks. (Yes, we finally have a definitive statement as to how NIBs should be released!) The one exception is that a window with "release on close" will be released automatically. Also, keep in mind that NSWindowController doesn't necessarily release all these top level items, so you should keep any eye on what it is doing. The new top level, windowless view is to allow developers to instantiate a NSView subclass without having to put it in a window and then pull it out of that window and move it elsewhere in code. Just create the top level view and hook it up. This is great for things like NSDrawer content views. To create a windowless view, simply drag an NSView subclass from the palette and drop it into the nib's instances pane. Be very careful with reference counting on these to avoid leaks! If you need to run some custom initialization code when a nib file is loaded, then this code should be inside the -awakeFromNib method of the object in question. You should not rely upon -init, -initWithFrame:, or -initWithCoder: to have any of the object's outlets initialized yet. When -awakeFromNib is called, all the outlets, targets, and actions will be set up and all the nib objects will be unarchived. The nibtool program is a very useful tool for manipulating nib files from scripts and the command line. The man page was just updated, so we even stand a chance of figuring out how to use it fully. One thing it can do is create an ASCII representation of a nib file, which is used by FileMerge to do diffs between nib files. Apple is also using the Nib Tool internally to streamline the localization process. Basically, you can use Nib Tool to create a strings file with all the strings found in the nib file. That file can be localized and then fed back to the Nib Tool with the original nib and a new, localized nib will be spit out. The localized nibs will not have the UI layout changed in any way, however, so you may still want to open it to adjust the control sizes to make them look better. Apparently, Apple has tried to implement the automatic resizing, but results were not what they wanted, so it was yanked. They may possibly attempt to do this in the future, however. Node:A data-link addressable entity on a network. Such as LaserWriter or a Macintosh or even a workstation. Network processes running within a node are called sockets and are assigned socket numbers. Node ID:See node identifier. Node Identifier (Node ID):An 8-bit number that, when combined with the AppleTalk network number of a node, is used to uniquely identify each node on a network. Noise-Equivalent Power (NEP):In a fiber-optic receiver, NEP represents the amount of optical power needed to produce an electric current as strong as the receiver's base noise level. Nonfunctional Requirements: (UML)General qualities of the system or constraints to which the system must conform. Examples of nonfunctional requirements are requirements related to the usability, reliability, performance, and supportability of the system. NTFS (NT File System):NTFS is the native file system for Windows NT. NTFS features include the following:
NuBus is a bus specification that provides expansion capabilities for later Macintosh models, i.e., Macintosh IIfx. Based on a Texas Instruments design, the NuBus is a general-purpose bus that supports 32-bit data and address transfer. This bus connects to the Macintosh using a 96-pin DIN connector. NuBus slots can be used to provide video capabilities (for example, color), extra memory, and networking capabilities. NuBus cards are self-configuring, and all NuBus expansion slots map to different internal addresses. To communicate with an expansion board, an application or process writes to a memory location associated with the board. Null Modem:A serial cable and connector with a modified pin configuration, compared to an ordinary RS-232 cable. The null modem enables two computers to communicate directly (without modems as intermediaries). A null modem cable is also known as an asynchronous modem eliminator (AME). The figure "Null Modem Pin Assignments" below shows the pin assignments for the various 9- and 25-pin combinations used on PCs. NULL MODEM PIN ASSIGNMENTS: 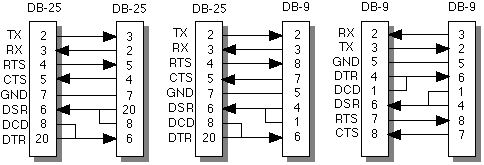
Numbering System: In a telephone network the hierarchical network topology of the telephone network is complemented by a hierarchical decimal numbering system for dialing connections within the network. For example in the 10-number system used in North America, the area code specifies a subarea that has been assigned a three-digit number. The next three numbers are the exchange code, which identifies specific switching facilities in a central office within the subarea. The final four digits specify a specific line that connects the user to the central office. Nyquist Interval:In telecommunication, the Nyquist interval is the maximum time interval between equally spaced samples of a signal that will enable the signal waveform to be completely determined. Note 1: The Nyquist interval is equal to the reciprocal of twice the highest frequency component of the sampled signal. Note 2: In practice, when analog signals are sampled for the purpose of digital transmission or other processing, the sampling rate must be more frequent than that defined by Nyquist's theorem, because of quantization error introduced by the digitizing process. The required sampling rate is determined by the accuracy of the digitizing process. Nyquist-Shannon sampling theorem:The Nyquist-Shannon Sampling Theorem is a fundamental tenet in the field of information theory, in particular telecommunications. The theorem states that, when converting from an analog signal to digital (or otherwise sampling a signal at discrete intervals), the sampling frequency must be applied to the original signal such that the sampled version is the same (perfectly) as the original signal. It is also Stated as: IN ORDER TO PERFECTLY REPRESENTED BY ITS SAMPLES, A SIGNAL MUST BE SAMPLED AT A SAMPLING RATE EQUAL TO AT LEAST TWICE ITS HIGHEST FREQUENCY COMPONENT. If the sampling frequency is less than this limit, then frequencies in the original signal that are above half the sampling rate will be "aliased" and will appear in the resulting signal as lower frequencies. Therefore, an analog low-pass filter is typically applied before sampling to ensure that no components with frequencies greater than half the sample frequency remain. This is called an "anti-aliasing filter". The theorem also applies when reducing the sampling frequency of an existing digital signal. The theorem was first formulated by Harry Nyquist in 1928 ("Certain topics in telegraph transmission theory"), but was only formally proved by Claude E. Shannon in 1949 ("Communication in the presence of noise"). Mathematically, the theorem is formulated as a statement about the Fourier transform. If a function s(x) has a Fourier transfrom F[s(x)] = S(f) = 0 for |f| > W (Bandwidth), then it is completely determined by giving the value of the function at a series of points spaced 1/(2W) apart. The values sn = s(n/(2W)) are called the samples of s(x). The minimum sample frequency that allows reconstruction of the original signal, that is 2W (twice the bandwith) samples per unit distance, is known as the Nyquist frequency, (or Nyquist rate). The time inbetween samples is called the Nyquist interval. If S(f) = 0 for |f| > W, then s(x) can be recovered from its samples by the Nyquist-Shannon Interpolation Formula. From this we get the sampling rate of fs = 2W. Thus, the minimum sampling rate ( or lowest acceptable sampling frequency) for any audio or analog waveform is, according to this theorem, equal to twice the bandwidth of the signal. For exaple, with a 1250 Hz audio or analog signal, we see that we should sample it at a rate which is at least: fs = (2) x (1250 Hz) = 2500 Hz, or 2500 samples per second.
| |||||||||||||||||||||||||||||||||||||||||||||||||||
| Back | Home | Top | Feedback | Site Search |
 E-Mail Me |
This site is brought to you by This page was last updated on
09/18/2005 |
This Page has been accessed "23654" times.